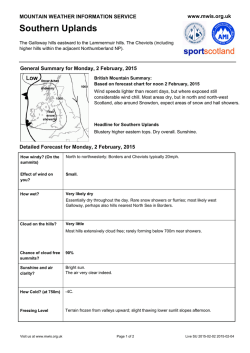
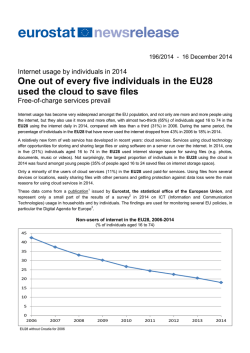
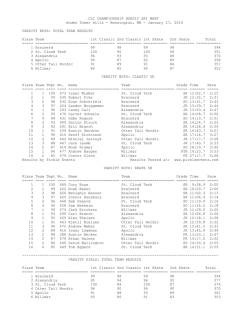
View PDF - IEEE Computer Society
*** Call for Papers *** Cloud Security Engineering Special Issue of IEEE Transactions on Cloud Computing As the use of cloud computing grows throughout society in general, it is essential that cloud service providers and cloud service users ensure that security and privacy safeguards are in place. There is, however, no perfect security and when a cybersecurity incident occurs, digital investigation will require the identification, preservation and analysis of evidential data. This special issue is dedicated to the identification of techniques that enable security mechanisms to be engineered and implemented in Cloud-based systems. A key focus will be on the integration of theoretical foundations with practical deployment of security strategies that make Cloud systems more secure for both end users and providers – enabling end users to increase the level of trust they have in Cloud providers – and conversely for Cloud service providers to provide greater guarantees to end users about the security of their services and data. Significant effort has been invested in performance engineering of Cloud-based systems, with a variety of research-based and commercial tools that enable autoscaling of Cloud systems, mechanisms for supporting Service Level Agreement-based provisioning and adaptation and more recently for supporting energy management of large scale data centres. This special issue will be devoted to understanding whether a similar engineering philosophy can be extended to support security mechanisms, and more importantly, whether experience from the performance engineering community (who often need to carry out analysis on large log files) can be carried over into the security domain. We encourage authors to be exploratory in their papers – reporting on novel use of performance engineering tools that could be repurposed for supporting security management and vice versa. This special issue will focus on engineering strategies that enable Cloud security to be supported. Papers which describe how a security solution has been implemented in a practical system will be given greater preference to those that primarily discuss theoretical foundations. Topics of interest include: • Advanced security features • Anonymity • Cloud forensic and anti-forensic techniques and implementations • Cloud privacy • Cloud-based honeypots • • • • • • • Cloud-based intrusion detection and prevention systems Distributed authentication and authentication Implementation of cryptographic and key management strategies in clouds (e.g. homomorphic encryption for cloud computing) Multi-Cloud security provisioning Real time analysis of security (log) data for alert generation Remote collection of evidence (e.g. from cloud servers) Security-focused Service Level Agreements High quality survey papers on the above topics are also welcome. Important Dates (Tentative Schedule) • Submission deadline: March 31, 2015 • Authors’ notification: May 31, 2015 • Revisions due: July 31, 2015 • Final decision: August 31, 2015 • Camera ready version due: October 30, 2015 • Tentative publication date: January – February 2016 Submission Information The special issue invites original research papers that make significant contributions to the state-of-the-art in “Cloud Security Engineering”. The papers must not have been previously published or submitted for a journal or conference publication. However, the papers that have been previously published with at international, peer reviewed conferences could be considered for publication in the special issue if they contain significant number of “new and original” ideas/contributions along with over 40% new material added to the contribution. Authors should explicitly identify where the previous version of the paper has been published (or submitted) and what this additional 40% content includes. Submissions must be directly submitted via the IEEE TCC submission web site at https://mc.manuscriptcentral.com/tcc-cs, and must follow instructions for formatting and length listed there. For additional information, please contact Omer Rana at [email protected] Selection and Evaluation Criteria - Significance to the readership of the journal - Relevance to the special issue - Originality of idea, technical contribution, and significance of the presented results - Quality, clarity, and readability of the written text - Quality of references and related work - Quality of research hypothesis, assertions, and conclusion Editor-in-Chief Rajkumar Buyya, The University of Melbourne, Australia Guest Editors Kim-Kwang Raymond Choo, University of South Australia, Australia Email: [email protected] Google Scholar: http://scholar.google.com.au/citations?user=rRBNI6AAAAAJ&hl=en Omer Rana, Cardiff University, UK Email: [email protected] Google Scholar: http://scholar.google.com.au/citations?user=TboOBAMAAAAJ&hl=en Muttukrishnan Rajarajan, City University London, UK Email: [email protected] Google Scholar: http://scholar.google.com.au/citations?user=gJ5yqXwAAAAJ&hl=en
© Copyright 2026