Programme
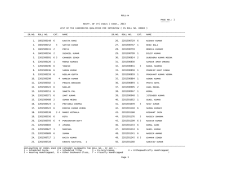
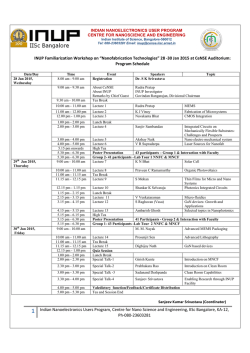
International Conference on Distributed Computing and Internet Technology (ICDCIT-2015) Conference Schedule 5th – 8th February, 2015 KIIT University, Bhubaneswar, India Confrence Hall-4, Campus-6 Day 1: 5th February 2015 09:00 - 09:45 A.M Registration Industry Symposium 09:45 - 10:45 A.M 10:45 -11:00 A.M 11:00 - 12:00 A.M 12:00 - 01:00 P.M Big Data Architecture Bhashyam Ramesh Tea Break Big Data Search and Mining P. Radhakrishna Applications of BigData Hareesh Boinepelli 01:00 - 01:15 P.M Inauguration of PIC 01:15 - 02:00 P.M Lunch 02:00 - 03:40 P.M Distributed Computing and Algorithms Finding RkNN Set in Directed Graphs Pankaj Sahu, Prachi Agrawal, VikramGoyal and DebajyotiBera Gathering Asynchronous Robots Under Nonuniform Limited Visibility Avik Chatterjee, SrutiGanChaudhuri and KrishnenduMukhopadhyaya A Routing Calculus with Flooding Updates Manish Gaur, Ian Mackie and Simon Gay k-Distinct Strong Minimum Energy Topology Problem in Wireless Sensor Networks BhawaniSankar Panda, D. Pushparaj Shetty and Arti Pandey Path Planning Algorithm for Mobile Anchor in Connected Sensor Networks Kaushik Mondal, ArindamKarmakar and ParthaSarathi Mandal 03:40 - 03:55 P.M 04:00 - 05:00 P.M Tea Break Invited Talk – 1 :Checking Cloud Contracts in Microsoft Azure NikolajBjorner Day 2: 6th February 2015 09:00 - 09:30 A.M 09:30 -11:00 A.M Registration Secure Computing and Communication – 1 Repetition Pattern Attack on Multi-word-containing SecureString 2.0 Objects Gunter Fahrnberger Computationally Secure Cheating Identifiable Multi-Secret Sharing for General Access Structure ParthaSarathi Roy, Angsuman Das and AvishekAdhikari S-Gossip: Security enhanced Gossip Protocol for Unstructured P2P Networks SumitTetarave, SomanathTripathy and SathyaPeri k-degree Closeness Anonymity: A Centrality Measure Based Approach for Network Anonymization DebasisMohapatra and ManasRanjanPatra 11:00 -11:15 A.M Tea Break 11:15 - 12:15 A.M Invited Talk – 2 Models of Circular Causality G. Michele Pinna 12:15 - 01:15 P.M Invited Talk – 3: Geo-indistinguishability: A Principled Approach to Location Privacy CatusciaPalamidessi 01:15 - 02:30 P.M Lunch 02:30 - 03:50 P.M Internet Technologies and Web Services Time and Cost Aware Checkpointing of Choreographed Web Services Vani VathsalaAtluri and HrushikeshaMohanty A Preprocessing of Service Registry : Based on I/O Parameter Similarity H. N. Lakshmi and HrushikeshaMohanty Financial Risk Management in e-commerce using Executable Business Process Modeling Notation RamkumarIyer and SanjeeviMoorthy DILT A Hybrid Model for Dynamic Composition and Execution ofHeterogeneous Web Services KanchanaRajaram, ChitraBabu and AkshayaGanesan 03:50- 04:05 P.M 04:10 - 05:10 P.M Tea Break Invited Talk – 4 : Fusing Sensors for Occupancy Sensing in Smart Building Krithi Ramamritham 05:10 - 06:00 P.M Poster presentation 0600 - 07:00 P.M 07:00 - 08:00 P.M 08:00 - 09:30 P.M Inaugural function Cultural Programme Conference Dinner Day 3: 7th February 2015 09:00 - 09:30 A.M Registration 09:30 -10:30 A.M Information Retrieval and Recommender Systems - 1 Predicting Post Importance in Question Answer Forums based on Topic-wise User Expertise DeepaAnand and FebinVahab SQLiDDS: SQL Injection Detection using Query Transformation and Document Similarity DebabrataKar, SuvasiniPanigrahi and SrikanthSundararajan Information Retrieval in Wikipedia with Conceptual Directions Julian Szymanski 10:30 -10:45 A.M 10:45 - 11:45 A.M Tea Break Invited Talk – 5: Discrete Control-based Design of Adaptive and Autonomic Computing Systems Eric Rutten 11:45 - 12:45 P.M Invited Talk – 6: Privacy and Security Challenges in Internet of Things ManikLal Das 12:45 - 02:00 P.M Lunch 02:00 - 03:00 P.M Secure Computing and Communication – 2 Cloud Computing A Chinese Remainder Theorem based Key Management algorithm for Hierarchical Wireless Sensor Network PranaveBhaskar and Alwyn Pais Design and Development of Secure Cloud Architecture for Sensor Services R. S. Ponmagal, N. Dinesh and Uma Rajaram An Evolutionary Computation based Classification Model for Network Intrusion Detection AshalataPanigrahi and ManasRanjanPatra Cloud Federation Formation Using Coalitional Game Theory Benay Kumar Ray, SunirmalKhatua and Sarbani Roy Intrusion Detection in a Tailor-Made Gaussian Distribution WirelessSensor Networks Amrita Ghosal and SubirHalder 03:00- 03:15 P.M 03:15 - 04:15 P.M Tea Break Invited Talk – 7: Gappy Total Recaller: Efficient Algorithms and Data Structures for Accurate Transcriptomics B. Mishra 04:15 - 5:15 P.M Invited Talk – 8: Designing for Scalability and Trustworthiness in mHealth Systems Sanjiva Prasad 05:15 - 6:15 P.M Poster presentation Day 4: 8th February 2015 09:00 - 09:30 A.M 09:30 -10:10 A.M Registration Societal Applications Predicting User Visibility in Online Social Network using Local Connectivity Properties Nemi Chandra Rathore, SomanathTripathy and Joydeep Chandra Information Retrieval and Recommender Systems - 2 Query Execution for RDF Data on Row and Column Store TruptiPadiya, MinalBhise, Sandeep Vasani and Mohit Pandey A Concept for Heterogeneous Recommender System Based on Blackboard Architecture Rohit Gupta and Anil Kumar Singh Using kNN and SVM based One-Class Classiffier for Detecting Online Radicalization on Twitter Swati Agrawal and Ashish Sureka 10:10 - 10:25 A.M 10:30 -11:30 A.M Tea Break Invited Talk – 9: Consumer Genomics to Genomic Medicine: Role of Discrete Algorithms Laxmi Parida 11:30 -12:30 P.M Invited Talk – 10: Enabling Electronic Participation - From Cases to Tools Elsa Estevez 01:00- 02:00 P.M Lunch 02:00 - 04:20 P.M Student Symposium Prolonging the Network Lifetime of Heterogeneous WSNs Using MECRSEP Shobti Saini, Meenakshi Sharma Image Steganography using Index Based Logistic Mapping Shreenandan Kumar, Suman Kumari, Sucheta Patro, Tushar Shandilya Finding Tweet Events Abhaya Kumar Pradhan, Hrushikesha Mohanty Handwritten and Printed Text Discrimination in Kannaa Document Images Rajmohan Pardeshi Stochastic Modelling of The Routing Calculi Rama Kant, Manish Gaur A Survey on Formal Modelling for Secure Routing in Mobile Ad hoc Networks Parul Yadav, Manish Gaur Evolving Sentiments towards e-Governance using Opinion Mining Pankaj Kumar, Alisha Jaidi, Ankita Srivastava, Geet Jain 04:20 - 04:35 P.M 04:45- 05:15 P.M Tea Break Valedictory Poster Session – 1 (6th February, 2015 - 5.15 PM to 6.15 PM) 1. Application of Soft Computing Technique for Web Service Selection Debendra Kumar Naik, SmitaKumari and Santanu Kumar Rath 2. Weighted Load Balanced Adaptive Gateway Discovery in Integrated Internet MANET Rafi U. Zaman and Khaleel Khan 3. Slice Based Testing of CGI Based Web Applications MadhusmitaSahu and Durga Prasad Mohapatra 4. An Efficient Resource Allocation Algorithm for IaaS Cloud Sanjaya Kumar Panda and Prasanta K. Jana 5. Genetic Algorithm Framework for Bi-objective Task Scheduling in Cloud Computing Systems A.S. AjeenaBeegom and M. S. Rajasree 6. Optimal Cloud Resource Provisioning: A Two-Criteria Formulation GeetikaMudali, ManasRanjanPatra, K. Hemant Kumar Reddy and Diptendu Sinha Roy 7. A Fuzzy Computationally Intelligent System for Resource Allocation in WIMAX Akashdeep Sharma 8. Improving Activity Prediction and Activity Scheduling in Smart Home Networks for Enhanced QoS KoteswaraVemu Poster Session – 2 (7th February, 2015 - 5.15 PM to 6.15 PM) 9. SMCDCT: A Framework for Automated MC/DC Test Case Generation using Distributed Concolic Testing SangharatnaGodboley, Subhrakanta Panda and Durga Prasad Mohapatra 10. On-the-fly Symmetry Reduction of Explicitly Represented Probabilistic Models Reema Patel, Kevin Patel and Dhiren Patel 11. SecureString 3.0 - A Cryptosystem for Blind Computing on Encrypted Character Strings Gunter Fahrnberger and Kathrin Heneis 12. A Secure Image Hashing Technique for Forgery Detection TanmoyKanti Das and PiyushKantiBhunre 13. Co-occurrence and Semantic Similarity Based Hybrid Approach for Improving Automatic Query Expansion in Information Retrieval Jagendra Singh and Aditi Sharan 14. Analysis of Emergency Evacuation of Building using PEPA Anil Kumar Singh and Surinder Kaur 15. Data Mining on ICT Usage in an Academic Campus: A Case Study Ajay Auddy and SripatiMukhopadhyay 16. A Theory On Genesis and Spread of Corruption HrushikeshaMohanty 17. Social network analysis of different parameters derived from real time profile ParamitaDey, Aniket Sinha and Sarbani Roy
© Copyright 2026