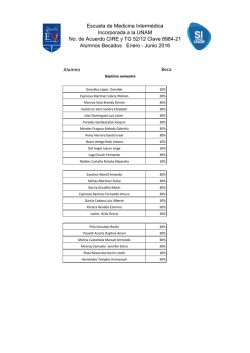
here - Tecnológico de Monterrey
Curriculum Vitae Raúl Monroy July 19, 2015 General Information Nationality: Phone Number: Fax Number: e-mail: URL: Mexican +52 (55) 5864 5316 +52 (55) 5864 5751 [email protected] http://homepage.cem.itesm.mx/raulm University Education and Degrees Awarded 1993-98: PhD in Artificial Intelligence. Thesis: Planning Proofs of Correctness of CCS Systems, under the supervision of Prof. Alan Bundy and Dr. Ian Green, and examined by Prof. Matthew Hennessy and Dr. Alan Smaill. The University of Edinburgh. 1992-1993: MSc in Information Technology. Thesis: The Use of Abduction to Correct Faulty Conjectures, under the supervision of Prof. Alan Bundy, Dr. Jane Hesketh and Dr. Andrew Ireland. The University of Edinburgh. 1987-1990: MSc in Computer Systems. Thesis: TEC-XINU, an Operating System, under the supervision of Dr. Ralf Eder. Instituto Tecnológico y de Estudios Superiores de Monterrey, at State of México (Mexico). 1980-1985: BSc in Electronics. Thesis: A VLSI-Based Short Distance Modem, Using Manchester Code, under the supervision of Dr Emmanuel Moya. Universidad Autónoma Metropolitana, Ixtapalapa (Mexico). Additional training The 1994 International Marktoberdorf Summer School: (organised by NATO) 8 courses lectured by Prof. E.W. Dijkstra, Prof. Tony Hoare, Prof. Allain Martin, Dr. Martin Abadi, Prof. Michael Fourman, Prof. Frederick Schneider, Prof. Manfred Broy, Prof. David Gries, Prof. Samson Abramsky. 1 Parallel Processing: Oklahoma State University at Stillwater. Summer 1990, (50 Hrs), lectured by Dr. K.M. George. Artificial Intelligence: Oklahoma State University at Stillwater. Summer 1990, (50 Hrs), lectured by Dr. B. Mayfield. Object-Oriented Software Construction: Oklahoma State University at Stillwater. Summer 1992, (50 Hrs), lectured by Dr. K.M. George. Advanced Artificial Intelligence: Oklahoma State University at Stillwater. Summer 1992, (50 Hrs), lectured by Dr. D. Miller. Object-Oriented Programming: ITESM, 1990, lectured by Dr. Bertrand Meyer. Quality Control: ITESM. Certified as total quality control manager (250 Hrs) Languages Spanish: Mother tongue English: Fluent: IELTS score = 8 (1996), TOEFL score = 637 (2008), TOEIC score = 925 (1998) Career since Graduation 2014-date: Tecnológico de Monterrey, Escuela nacional de ingenierı́a y ciencias, Leader of the Information Technology Research Group. 2010-date: Tecnológico de Monterrey, Campus Estado de México, (Full) Professor in Computer Science. 2007-2009: Tecnológico de Monterrey, Campus Estado de México, Associate Professor in Computer Science. 2007-2007: DFKI, Saarbrücken, Germany, Associate and Visiting Researcher. 2006-2007: University of Edinburgh, Edinburgh, Scotland, Visiting Researcher (on sabbatical leave from ITESM CEM). 2000-2007: Tecnológico de Monterrey, Campus Estado de México, Associate Professor in Computer Science. 1992-1999: Tecnológico de Monterrey, Campus Estado de México, Assistant Professor in Computer Science. 1992-1997: Tecnológico de Monterrey, Campus Estado de México, Leave of Abscence. 1985-1992: Tecnológico de Monterrey, Campus Estado de México, Lecturer in Computer Science. 2 1984: Universidad Autónoma Metropolitana, Part time faculty member. Electrical Engineering Department. Teaching Responsibilities My workload consists of 40% teaching, 10% administration and 50% research. I teach only in two terms out of three offered in an academic year. I have been involved in teaching since 1984. I do enjoy teaching. Throughout all these years, I have taught several many courses, including electric circuits, electronics, digital systems, computer organisation, assembly language, computer architecture, computer networks, artificial intelligence, knowledge representation, operating systems, common sense reasoning, logic, probability, quantitative modelling and simulation, numerical analysis, communication and concurrency, computer security, and many other more. During the last five years, I have designed, developed or taught the following courses in computing: undergradate: Quantitative Methods and Simulation, Formal Methods in Software Engineering, Operating Systems, Introduction to Communication and Concurrency, Computer Security, and Numerical Analysis; and graduate: Logic and Probability, Formal Methods in Computer Security, Automated Reasoning and Communication and Concurrency. Research Interests I am interested in automating the use of theorem proving to formal methods of system development. I have recently become interested in issues of computer security and robotics. Currently, my research concerns: • The automated repair of security protocols; • The discovery and application of general search control strategies for uncovering and correcting errors in either a system or its specification; • The design of novel methods for computer intrusion detection; and • The design of novel methods for motion planning (sensor-based robotics.) The main techniques for these lines of investigation have been proof planning, the productive use of failure and process algebras. Quoting Alan Bundy, proof planning is a method that uses an explicit representation of the overall shape of a family of similar proofs. The productive use of failure is collecting evidence of theory misconception and mal-formulation in order to pinpoint flaws and suggest theory development. Process algebras provides a means for modelling, building and analysing communicating systems in terms of a few primitive ideas; they are well-established, both in Industry and in Academia, and have evolved into an ISO-standard, LOTOS. In 2003, I founded the Computer Networking and Security Group (NETSEC), a research group based at Tecnológico de Monterrey. NETSEC is a group 3 of computer scientists with interests in intrusion detection and security of computer networks and automated analysis (and possibly correction if faulty) of security protocols. This group comprehends 4 principal investigators, one postdoctoral participant, six research assistants and over a dozen of MSc students. Jointly, the group has published over 70 papers and graduated 27 students (3 PhD students, 18 MSc students, and 6 undegraduate students) since 2003. The group receives substantial funding from Tecnológico de Monterrey, and from CONACYT, for covering operation expenses, granting scholarships to graduate students and developing infrastructure. The group currently conducts its experiments in two laboratories, one is the computer networking, and the other one the mobile computing. For more information about the Networking and Security Group, the reader is referred to the group’s URL: http://www.cem.itesm.mx/investigacion/seguridad/ Recently, I have been appointed to the Chair of Information Technology, a distributed research group, which includes a number of people, including: Julieta Noguez, Lourdes Muñoz, Moisés Alencastre, Miguel González, Neil Hernández, Jaime Mora, Gildardo Sánchez, Luis A. Trejo and Edgar Vallejo, amongst others. Research Grants Held 2015: Formal Verification of Web Applications, Google Faculty Research Awards, (Principal Investigator) with D. Hutter and Victor Ferman. 2014-date: Information Technology, ITESM, School of Science and Engineering, Research group grant (Principal Investigator); 2007—2013: Aspects of Computer Security, ITESM—Rectorı́a Zona Centro del Sistema ITESM, Grant C-CEM-04/07 (Principal Investigator); 2010—2013: Aplicación de Modelos Estadı́sticos y Técnicas de Caracterización a Tráfico de Red para la Detección de Intrusos, Convocatoria SEP Investigación Básica 2008, Grant 105698 (Principal Investigator); 2010—2013: Automated Repair of Industrial-Strength Security Protocols, Convocatoria Cooperación Bilateral 2009, Grant 121596, (Principal Investigator) with Dieter Hutter (also Principal Investigator); Completed Projects 2010—2012: Planificación de Movimientos y Percepción para Robots: Mundos Tridimensionales y Manejo de Incertidumbre, Convocatoria SEP Investigación Básica 2008, Grant 106475 (Associate Investigator); 2010—2012: ELISA - Sistema de Localizacin y Asistencia Inmediata, CUDICONACYT (Associate Investigator); with Luis A. Trejo 4 2005—10: On the Timely Detection of Mimicry Attacks, CONACyT. Convocatoria SEP Investigación básica, Grant 47557 (Principal Investigator). 2008: Método estadı́stico de detección de ataques al DNS. Fondo Regional para la Innovación Digital en América Latina y el Caribe (FRIDA) 2007 (Associate Investigator); 2007—8: Pursuit Evasion Problems in 3D Environments. CONACyT — National Science Foundation (NSF). Grant J110.534/2006 (Associate Investigator); 2007: On Automatically Patching Faulty Security Protocols. Consejo Nacional de Ciencia y Tecnologı́a (CONACyT) — Deutscher Akademischer Austausch Dienst (DAAD). Grant J110.382/2006 (Principal Investigator), with Dieter Hutter (also Principal Investigator); 2005—6: On the Timely Detection of Mimicry Attacks, Fondo Regional para la Innovación Digital en América Latina y el Caribe (FRIDA) 2005 Grant VI (Principal Investigator); 2003—6: Aspects of Computer Security, ITESM—Consorcio Interrectorı́as Grant CCEM- 0302-05 (Principal Investigator); 2002—4: Computer Security Based on Immune Systems, together with Dieter Hutter from DFKI, Germany. CONACyT-BMBF Grant J200.1442/2002 (Principal Investigator); 2001—4: The Use of Proof Planning to Automating the Verification of Authentication Protocols, CONACyT Grant 33337-A (Principal Investigator); 1997—2001: The Use of Proof Planning to Automate Theorem Proving to Formal Methods of System Development, together with Francisco Cantú and Santiago Negrete. CONACYT REDII (Principal Investigator). While doing my PhD, I was associated with the following project: 1992—7: Communication in safety cases: a semantic approach, SERC Grant GR/J/58619. Research Supervision Research Assisstants (Post-doctorates) 1. Dr. Carlos Arturo Hernández Gracidas, graduated from INAOEP, is carrying out research, following my ideas on Masquerade Detection. Funded by CONACYT (2011 — 2012). 2. Dr. Miguel Angel Medina Pérez, graduated from INAOEP, is carrying out research, following my ideas on Masquerade Detection. His research stay is funded by ITESM, and lasts one year, starting from January 16, 2015. 5 PhD Students 1. Jorge Rodrı́guez Ruiz; Jorge is aiming at detecting malware using a model inspired on biological immune systems; admitted January 2014; 2. Eduardo Aguirre Bermúdez; Eduardo is aiming at providing privacy to android-based mobile devices; admitted August 2013; 3. José Benito Camiña Prado; Benito is aiming at extending his results on Masquerade Detection using Navigation Structures; admitted January 2012. 4. Vı́ctor Hugo Ferman Landa; Vı́ctor is aiming at a method for automated browser-based security protocol analysis; admitted January 2011. 5. Jorge Martı́nez Muñoz; Jorge is working on extending Juan Carlos’s tool, called shrimp, to automatically repair faulty protocols of type group; admitted August 2008; 6. Rosa Elena di Constanzo Lorencez; Rosa Elena is working on a tool capable of detecting vulnerabilities on security protocols; admitted August 2008; 7. Jorge Vázquez Islas; Jorge is aiming at a method for detecting attacks to 802.11; admitted August 2008; 8. Roberto Alonso Rodrı́guez; Roberto is continuing his MSc projects, studying a social characterisation of DNS usage to DNS DoS attack detection; awarded May 2015; 9. Karen Azurim Garcı́a Gamboa; Karen was associated with the project ‘On the Timely Detection of Mimicry Attacks’, admitted May 2005, examined December 2010; awarded May 2011. 10. Juan Carlos López Pimentel, ‘On the Automated Correction of Faulty Security Protocols’: admitted January, 2004; examined April, 2008; awarded May 2008; and 11. Fernando Godı́nez Delgado, ‘On an Efficient and Scalable Architecture for Mimicry Attacks Detection Using Probabilistic Methods: admitted July, 2000; examined November, 2004; awarded May, 2005; MSc Students 1. Jorge Rodrı́guez Ruiz. Detección de impostores en la base WUIL-DS. ITESM CEM; awarded December, 2013. 2. José Benito Camiña Prado, Hacia la detección de intrusiones mediante el análisis del comportamiento del usuario en su sistema de archivos, awarded May 19, 2011. 6 3. Eduardo Aguirre Bermúdez, Modelado de ataques computacionales a “host” utilizando redes de Petri coloreadas, awarded May 19, 2011. 4. José Ernesto Buelna Sánchez, Verificación de Polı́ticas de Integridad para Sistemas Distribuidos en Tiempo Real, defended April 28, 2010, awarded May 2010; 5. Roberto Alonso Rodrı́guez, Modelos estadı́sticos y de IA para la detección de intrusiones y caracterización de tráfico, defended January 2010 (cosupervisor), awarded May 2010; 6. Ricardo Farrera Saldaña, ‘Análisis y Caracterización de Tráfico en Internet’, defended November 2009, awarded December 2009 (cosupervisor); 7. Armando Aguayo Mendoza, ‘La Monitorización de la Polı́tica de Seguridad de Procesos Mediante Correlación de Eventos’, defended November 2009, awarded December 2009 (co-supervisor); 8. Cuauhtémoc Juan Portas Sánchez, ‘Validación de Polı́ticas de Seguridad en una Red Financiera Mediante Correlacion de Eventos’, defended November 2009, awarded December 2009 (co-supervisor); 9. Anna Valeska Álvarez Béjar, ‘Administrador de Polı́ticas de Seguridad: 2nda Versión’, defended June 2006, awarded December 2006; 10. Vı́ctor Hugo Garcı́a Pichardo, ‘Algoritmo ID3 en la Detección de Ataques en Aplicaciones WEB’, awarded May 2006; 11. Karen Azurim Garcı́a Gamboa, ‘Administrador de Polı́ticas de Seguridad’, awarded January, 2005; 12. Juan Carlos López Pimentel, ‘Verificación Formal de Protocolos de Seguridad en HOL usando el Método Inductivo’, awarded September, 2004; 13. Rosa Saab Asbun, ‘Modelo de un Sistema Inmunológico Natural en Álgebra de Procesos’, awarded September, 2002; 14. Alberto Calixto Simón, ‘Análisis del protocolo TLS’, awarded September, 2001; 15. Maya Carrillo Ruiz, ‘Lógicas de Autenticación Aplicadas al Estudio de Protocolos’, awarded September, 2001; 16. Arturo Rodolfo Castro Lloera, ‘Sistema de Monitoreo Experto Aplicado a Equipos de Cómputo’, awarded December, 2000; 17. Enrique Alejandro Navarrete Paredes, ‘Reconocimiento de Patrones Aplicado a la Exposición Fotográfica’, awarded December, 1999. 7 18. Anabelem Soberanes, admitted January 2005; 19. Raymundo Eybar Piña, admitted January 2005. BSc Students 1. Mauricio Cunillé Blando. Admitted January 2015. 2. Leonardo Mauricio Cañete Sifuentes. Detección de impostores mediante estructuras de navegación, awarded December, 2014. 3. Axel Alejandro Gutiérrez Olivo. Detección de impostores mediante estructuras de navegación. Admitted August, 2014. 4. Eduardo Murillo González. Detección de impostores mediante estructuras de navegación, awarded June, 2012. 5. Jorge Rodrı́guez Ruiz. Detección de DLLs maliciosos. ITESM CEM, awarded May, 2011. 6. Luis Rodolfo Hernández Guzmán. Creación de un API para MATLAB para soporte en el análisis de matrices de co-ocurrencia. ITESM CEM, awarded December, 2010. 7. Velázquez, José Fernando. Caracterización de Ataques al DNS para la implementación de un IDS en un ambiente GRID. ITESM CEM, awarded November, 2008. 8. Garcı́a Garcı́a, Juan Francisco. Implementación de un programa registrador de eventos para la elaboración posterior de un detector de intrusos basado en el análisis del comportamiento del usuario en su interacción con el sistema de archivos. ITESM CEM, awarded May, 2009. Distinctions 2015: Network Security, Summer Course, University of Bremen, Visiting Professor. 2015: National academy of Computer Science. Founding member. 2014: Formal Verification of Web Applications, Google Faculty Research Awards, (Principal Investigator) with D. Hutter and Victor Ferman. 2013: COMIA 2013 2nd best paper award, SMIA; 2012-date: Associate editor of Journal Computación y Sistemas 2012-date: Associate editor of Journal Inteligencia Artificial (ISSN 19883064); 8 2012: COMIA 2012 2nd best paper award, SMIA; 2012: 3rd place for the Rómulo Garza Price for Outstanding Achievements in Science, Technology, and Engineering, ITESM 2012; 2012-2013: Coordinator of the CONACYT Research Network on Information Technology and Communication, REDTIC, 2012; 2010-2012: President of the Mexican Society for Artificial Intelligence; 2012-date: Member of the External Examination Committee to the National Research Centre for Mathematics, CIMAT, 2012; 2012: Member of IBERAMIA - Inteligencia Artificial Journal Editorial Board - ISSN 1988-3064; 2012: COMIA’12 2nd best paper award, Mexican Society for Artificial Intelligence (SMIA); 2011: Fellowship to the Mexican Academy of Sciences; 2010: Professorship at Tecnológico de Monterrey, Campus Estado de México; 2009-2012: Technical Committee Member of “Red Temática en Tecnologı́as de Información y Comunicaciones”, CONACYT; 1999-date: National Researcher, rank 2, subject area 7, CONACYT—SNI (12232); 2006: Sabbatical leave to carry out research on the “Automated Correction of Faulty Security Protocols”, Tecnológico de Monterrey, campus Estado de México; 2006: The Golden Ram Award for Investigation 2006, Tecnológico de Monterrey, campus Estado de México; 2006: Final to the Rómulo Garza Award, Sistema Tecnológico de Monterrey; 2000, 2002, 2005: Research Grants 33337-A, J200.1442/2002 and 47557, CONACyT; 2005: Research Grant VI, Fondo Regional para la Innovación Digital en América Latina y el Caribe (FRIDA); 2005: MICAI’05 best paper award, Mexican Society for Artificial Intelligence (SMIA); 2004: Candidate to best paper award, IBERAMIA’04; 2003—5: ITESM Research Group Grant CCEM- 0302-05, ITESM Consorcio Inter-rectorı́as; 9 2002: MICAI’02 best paper award, SMIA; 2000: Candidate to best paper award and invited to submit journal version to the journal of Automated Software Engineering, ASE’00; 1998: Candidate to best paper award and invited to submit journal version to the journal of Automated Software Engineering, ASE’98; 1994: NATO Scholarship to participate in the 1994 International Marktoberdorf Summer School, in Germany, NATO; 1993-1998: CONACyT scholarship to conduct studies towards a PhD, Artificial Intelligence, at Edinburgh University; 1992: CONACyT scholarship to conduct studies towards a MSc, Artificial Intelligence, at Edinburgh University; and 1987-1991: ITESM scholarship to conduct studies towards a MSc, Computer Systems, at ITESM. Administrative Experience and Committee Membership University Responsibilities • 2005-date: Session Track Organiser at the editions 35, 36, 38, 39, 40, 41, 42 and 43 of the Congreso de Investigación y Desarrollo Tecnológico del ITESM; • 2004-date: Member of the team that designed the 2005 BSc Programme in Computer Technology; • 2003-date: Leader of the research group called Computer Networking and Security; • 2004-date: Member of the PhD and the MSc Programme Committee in Computer Science; • 2001: Member of the team that designed the MSc Programme in Computer Science; • 1998, 2005, 7: Organiser of the MSc/PhD Programme Seminar; • 1997-1999: Organiser of the MSc Programme in Computer Science; • 1997: Leader of the team that designed the MSc Programme in Computer Science; • 1990-1992: Organiser of three MSc Programmes, one in Computer Systems, one in Information Systems, and one in Manufacturing; and 10 • 1990: Leader of the team that designed the MSc Programme in Computer Technology. External Responsibilities • 2012-2013: Coordinator of the CONACYT Research Network on Information Technology and Communication, REDTIC, 2012; • 2012-date: Member of the External Examination Committee to the National Research Centre for Mathematics, CIMAT, 2012; • 2012-date: Associate editor of Journal of Computación y Sistemas - ISSN 1405-5546; • 2012-date: Member of IBERAMIA - Inteligencia Artificial Journal Editorial Board - ISSN 1988-3064; • 2010-2012: President of the Mexican Society for Artificial Intelligence; • 2009-2012: Technical Committee Member of “Red Temática en Tecnologı́as de Información y Comunicaciones”, CONACYT; • 2007-date: Joint organiser of the MICAI workshop on computer security (2007, 2008 and 2009); • 1997-date: Served on the Program Committee of the following conferences: ENC’97, ENC’99, ENC’2010, MICAI’00, MICAI’02, MICAI’04, IBERAMIA’04, MICAI’05, MICAI’06, CITA’06, CORE’06, MICAI’07, CORE’07 MICAI’08, MICAI’09, MICAI’10, MICAI’11, and MICAI’12; • 2000-date: Served on Conference Committee of the following conferences: IJCAI’03, MICAI’00, MICAI’02, MICAI’04, MICAI’05, MICAI’06, MICAI’07, MICAI’08 and MICAI’09; • 1997-date: Served as an external reviewer for Convocatoria para Investigación Básica, organised by CONACyT; • 2005-date: Served on the CONACyT committee for the evaluation of applications to student scholarship extensions; • 1994-date: Served as a paper reviewer for the following journals: Expert Systems with Applications, Computación y Sistemas, Systems Man and Cybernetics, etc. • 1994-date: Served as a paper reviewer for the following conferences: CADE, LICS, IBERAMIA, ENC, IJCAI, IROS, ICRA, etc. • 2008-2010: Vice-president of the Mexican Society for Artificial Intelligence; • 2009: An editor of Springer-Verlag, LNAI series; 11 • 2009: Conference and Programme co-chairman of the 8th Mexican International Conference on Artificial Intelligence (MICAI’09), held in Guanajuato City, Mexico; • 2008: guest editor to “Computación y sistemas”; • 2008: Served as external reviewer for Convocatoria Bilateral, CONACyT; • 2008: MICAI local co-chair; • 2007: MICAI workshops co-chair; • 2006: Served on the 4th Seminar for the Development of the National Competitiveness; • 2005: Programme co-chairman of the 4th Mexican International Conference on Artificial Intelligence (MICAI’05), to be held in Monterrey, Mexico; • 2004: An editor of Springer-Verlag, LNAI series; • 2004: Programme co-chairman of the 3rd Mexican International Conference on Artificial Intelligence (MICAI’04), held in Mexico City, Mexico; • 2000-2006: Secretary Treasurer of the Mexican Society for Artificial Intelligence; • 2000-date: ACM member (7294044) • 2002: Joint organiser of the workshop on ‘Logic and Computation’, at TAINA’02; • 1999-2005: Served as a host researcher for Programa de Verano de Investigación Cientı́fica, organised by the Academia Mexicana de Ciencias. I have guided the research of about 15 students. • 1999: Joint organiser of the workshop on ‘Logic and Computation’, at ENC’99; Research Visits 1. May 18 — June 3, 2012: Deutsches Forschungszentrum für Künstliche Intelligenz (DFKI). Bremen, Germany; 2. May 29 — June 8, 2010: Deutsches Forschungszentrum für Künstliche Intelligenz (DFKI). Bremen, Germany; 3. June, 2009: INAOE. Puebla, México. 4. 2008—date: CIMAT, Guanajuato, México. 12 5. December 4—17, 2008: Deutsches Forschungszentrum für Künstliche Intelligenz (DFKI). Bremen, Germany; 6. January — March 2007: Deutsches Forschungszentrum für Künstliche Intelligenz (DFKI). Saarbrücken, Germany; 7. August — December, 2006 and then April — July, 2007: Centre for Intelligent Systems and Applications. The University of Edinburgh. Edinburgh, United Kingdom; 8. December 2005: 1 week at the DFKI, Saarbrücken, Germany; 9. December 2004: 2 weeks at the DFKI, Saarbrücken, Germany; 10. June 2004: 1 week at the University of Nottingham. Nottingham, United Kingdom; 11. July 2004: 1 week at the Universiyt of Edinburgh. Edinburgh, United Kingdom; 12. December 2003: 2 weeks at the DFKI, Saarbrücken, Germany; 13. December 2002: 2 weeks at the DFKI, Saarbrücken, Germany; 14. November 2002: 1 week at the University of Illinois at Urbana-Champaign. Urbana, USA; 15. July 2001: 1 week at the Technological University of Munich at Munich (Germany) and 1 week at the Universiyt of Edinburgh at Edinburgh (United Kingdom); 16. June 1999: 5 weeks at the University of Edinburgh at Edinburgh, United Kingdom; and 17. July 1994: 1 week at the Technological University of Darmstad. Darmstad, Germany. Publications Journal Papers (Indexed) 1. I. Becerra-Durán, R. Murrieta-Cid, R. Monroy, S. Hutchinson and J.P. Laumond. Maintaining Strong Mutual Visibility of an Evader Moving over the Reduced Visibility Graph. Autonomous Robots (AURO) In Press, 2015. 2. S.-M. Martı́nez-Monterrubio, J. Frausto-Solı́s and R. Monroy. EMRlog method for computer security for Electronic Medical Records with logic and data mining. BioMed Research International In Press, 2015. 13 3. C. del-Valle-Soto, C. Mex-Perera, R. Monroy, and J.-A. Nolazco-Flores. On the Routing Protocol Influence on the Resilience of Wireless Sensor Networks to Jamming Attacks. Sensors 15(4):7619-7649, MDPI, 2015. 4. J. Benito Camiña, C. Hernández-Gracidas, R. Monroy, and L. Trejo. The Windows Users and Intrusions Logs Dataset (WUIL-DS): An Experimental Framework for Masquerade Detection Mechanisms. Expert Systems with Applications, 41(3):919 - 930, Elsevier, 2014. 5. Ernesto Buelna and Raúl Monroy. Real-Time Verification of Integrity Policies for Distributed Systems. Journal of Applied Research and Technology, 11(6):831 - 843. 2013. 6. R. Alonso and R. Monroy. On the NP-Completeness of Computing the Commonality Amongst the Objects upon which a Collection of Agents has Performed an Action. Computación y Sistemas, 17(4):489 - 500. CIC - IPN, 2013. 7. K. A. Garcı́a, R. Monroy, L. A. Trejo, C. Mex-Perera, and E. Aguirre. Analyzing Log Files for Post-mortem Intrusion Detection. Journal of IEEE Transactions on Systems, Man, and Cybernetics — Part C 42(6):16901704. IEEE Computer Press, 2012. 8. I. Razo-Zapata, C. Mex-Perera, and R. Monroy. Masquerade Attacks Based on User’s Profile. Journal of Systems and Software 85(11):26402651, Elsevier, 2012. 9. R. Monroy. Editorial. Computación y Sistemas 16(4):379-381, CIC - IPN, 2012. 10. R. Monroy. Editorial. Polibits 46:3-4, CIDETEC - IPN, 2012. 11. R. Monroy, A. Bundy, and I. Green. On process equivalence = equation solving in CCS. Journal of Automated Reasoning 43(1):53-80, Springer, 2009. Springer. 12. R. Monroy and G. Arroyo-Figueroa. Editorial, Special Issue on Innovative Applications of AI. Computación y Sistemas 14(1):3-4, CIC del IPN, 2009. 13. J.C.-López P. and R. Monroy. Formal Support to Security Protocol Development: a Survey. Computación y Sistemas, special volume celebrating 50 years of Computing in Mexico, 12(1):89-109, CIC - IPN, 2008. 14. Juan C. López P., Raúl Monroy and Dieter Hutter. A method for patching interleaving-replay attacks in faulty security protocols. Electronic Notes in Theoretical Computer Science 174(4):117-130, Elsevier, 2007. 15. B. Tovar, L. Muñoz-Gomez, R. Murrieta-Cid, M. Alencastre-Miranda, R. Monroy and S. Hutchinson. Planning Exploration Strategies for Simultaneous Localization and Mapping. Journal Robotics and Autonomous Systems 54(4):314-331, Elsevier, 2006. 14 16. R. Monroy, R. Saab and F. Godı́nez. On Modelling an Immune System. Computación y Sistemas. 7(4):249–259, 2004. 17. Raúl Monroy. Predicate Synthesis for the Correction of Faulty Conjectures: the Proof Planning Paradigm. Automated Software Engineering, 10(3):247–269, 2003. 18. R. Monroy and A. Bundy. On the correction of faulty formulae. Computación y Sistemas, 5(1):25-37, 2001. 19. R. Monroy, A. Bundy, and I. Green. Planning Proofs of Equations in CCS. Journal of Automated Software Engineering 7(3):263–304, 2000. Edited Books • A. Hernández-Aguirre, R. Monroy and C.-A. Reyes-Garcı́a, editors, Proceedings of MICAI 2009: Advances in Artificial Intelligence, 8th Mexican International Conference on Artificial Intelligence, MICAI‘09, LNAI Vol. 5845, 2009. Springer. • A. Hernández-Aguirre, R. Monroy and C.-A. Reyes-Garcı́a, editors, Proceedings of the 8th Mexican International Conference on Artificial Intelligence, MICAI‘09, IEEE Computer Science Press. • R. Monroy, G. Arroyo-Figueroa, E. Sucar and H. Sossa, editors, Advances in Artificial Intelligence: Proceedings of the 3rd Mexican International Conference on Artificial Intelligence, MICAI‘2004, Springer-Verlag, Lecture Notes in Artificial Intelligence, Vol. 2972, 2004. • A. Gelbukh and R. Monroy, editors: Advances in Artificial Intelligence Theory, J. Research on Computing Science, Vol. 16, ISSN 1665-9899, IPN, 2005, printing 500; • A. Gelbukh and R. Monroy, editors: Advances in Artificial Intelligence Applications, J. Research on Computing Science, Vol. 17, ISSN 1665-9899, IPN, 2005, printing 500. Book Chapters • M. González-Mendoza and R. Monroy. Inteligencia Artificial. Chapter in, Julio Ernesto Rubio Barrios (ed.), Nuevas tendencias tecnológicas, Tecnológico de Monterrey. 2010. pp: 1-31. (in press) • A. de Albornoz, P. Escamilla-Velasco, R. Brena-Pinero, R. Monroy, R. Soto Rodrı́guez, S. Cerón-Alegre, M. Valenzuela-Rendón, E. VallejoClemente. Inteligencia Artificial. Chapter in Las Megatendencias Tecnológicas Actuales y su Impacto en la Identificación de Oportunidades Estratégicas de Negocios. ITESM. México. 2009. Grupo de Desarrollo Regional. pp: 105-117. 15 • R. Monroy, M. Alvarado and M. Osorio. Logic and Computation, Chapter in, H. Sossa and G. Arroyo, editors, MICAI/TAINA 2002, avances en inteligencia artificial. Centro de Investigación en Computación-IPN, 2002. • A. Aliseda and R. Monroy. Logic and Computation, Chapter in, J. M.Ahuactzin, editor, Encuentro Nacional de Computación, ENC‘99. Universidad de las Américas, 1999. Invited Papers 1. R. Monroy. Some Encounters on the Productive Use of a Failed Proof Attempt or a Counterexample. In, G. Sidorov, A. Hernández-Aguirre and C.-A. Reyes-Garcı́a, editors, Proceedings of the 9th Mexican International Conference on Artificial Intelligence, MICAI‘10, LNAI Vol. 6437, pp. 1 12, 2010. Springer. Conference Papers 1. J. B. Camiña, J. Rodrı́guez, and R. Monroy. Towards a Masquerade Detection System based on User’s Tasks. In, A. Stavrou, H. Bos and G. Portokalidis, editors, Proceedings of the 17th International Symposium on Research in Attacks, Intrusions and Defenses, RAID. LNCS vol. 8688, pp. 447 - 465. September, 2014. Springer. 2. J. C. López-Pimentel, V. Ramos Fon Bon and R. Monroy. A Web Service for Signing and Authenticating Digital Documents based on Symmetric Cryptography Protocol. International Journal of Digital Information and Wireless Communications (IJDIWC) 1(2): 434-444. The Society of Digital Information and Wireless Communications (SDIWC), 2012. 3. B. Camiña, R. Monroy, L. Trejo, and E. Sánchez. Towards Building a Masquerade Detection Method Based on User File System Navigation. In, I. Batyrshin, and G. Sidorov, editors, Proceedings of the 2011 Mexican International Conference on Artificial Intelligence, Part I, MICAI’11, LNCS vol. 7094, pp. 174 - 186, 2011. Springer. 4. J. C.-López-Pimentel, R. Monroy, and V. Ramos. Symmetric Cryptographic Protocol for Signing and Authenticating Digital Documents. In, V. Snasel and Y. Imai, editors, Proceedings of the 2011 International Conference on Digital Information Processing and Communications, ICDIPC’2011, LNCS (Communications in Computer Information Sciences Series) vol. 188, pp. 9-23, 2011. Springer. 5. Karen Garcı́a, E. Aguirre, R. Monroy and C. Mex-Perera. An Architecture for Forensic Intrusion Detection on System Logs. In, D. He, X. Chen and M. Reza-Abdi, editors, Proceedings of the 2010 International Conference on Information Security and Artificial Intelligence, ISAI 2010, pp. to appear, 2010. IEEE Computer Science Press. 16 6. I. Becerra, R. Murrieta-Cid and R. Monroy. Evader Surveillance under Incomplete Information. In Vijay Kumar, editor, Proceedings of the 2010 IEEE International Conference on Robotics and Automation, ICRA 2010, pp: to appear, IEEE Computer Science Press. 7. L.-A. Trejo, R. Alonso, R. Monroy, E. Sánchez, J. Vázquez, and M. Maqueo. Using Cloud Computing MapReduce operations to Detect DDoS Attacks on DNS servers. In Proceedings of 4th Iberian Grid Infrastructure Conference, IBERGRID 2010. 8. D. Hutter and R. Monroy. On the automated correction of protocols with improper message encoding. In, L. Vigan‘o and P. Degano, eds., Proceedings of the Joint Workshop on Automated Reasoning for Security Protocol Analysis and Issues in the Theory of Security, ARSPA-WITS’09, LNCS Vol. 5511, pages138-154. Springer, 2009. 9. R. Murrieta-Cid, R. Monroy, S. Hutchinson and J.-P. Laumond. A complexity result for the Pursuit-Evasion Game of Maintaining Visibility of a Moving Evader. In Proceedings of the 2008 IEEE International Conference on Robotics and Automation, ICRA’08, pages pages 2657-2664, USA, 2008. IEEE Computer Society Press. 10. Juan C. López P., Raúl Monroy and Dieter Hutter. On the Automated Correction of Security Protocols Susceptible to a Replay Attack. In, J. Biskup and J. Lopez, eds., Proceedings of the 12th European Symposium Research Computer Security, ESORICS 2007. LNCS Vol. 4734, pages 594-609, Germany, 2007. Springer. 11. C. Mex-Perera, R. Posadas, J.-A. Nolazco, R. Monroy, A. Soberanes and L. Trejo. An improved Non-negative Matrix Factorization Method for Masquerade Detection. In, R. Vázquez and J.-A. Dı́az, eds., Proceedings of the 1st Mexican International Conference on Informatics Security, MCIS 2006, Mexico, 2006. IEEE Computer Society Press. 12. R. Posadas, C. Mex-Perera, R. Monroy and J. A. Nolazco. Hybrid Method for Detecting Masqueraders Using Session Folding and Hidden Markov Models. In, A. Gelbukh and C. A. Reyes, eds., Proceedings of the 5th Mexican International Conference on AI, MICAI 2006, LNAI Vol. 4293, pages 622-631, Mexico, 2006. Springer. 13. Rafael Murrieta and Raúl Monroy. A Hybrid Segmentation Method Applied to Color Images and 3D Information. In, A. Gelbukh and C. A. Reyes, eds., Proceedings of the 5th Mexican International Conference on AI, MICAI 2006, LNAI Vol. 4293, pages 789-799, Mexico, 2006. Springer. 14. Anna A. Álvarez, Karen A. Garcı́a, Raúl Monroy, Luis A Trejo and Jesús Vázquez. A Tool for Managing Control Access Policies in Organisations. In, H. Yoshiura, K. Sakurai and K. Rannenberg, eds., Proceedings on the 17 1st International Workshop on Security, IWSEC 2006, LNCS Vol. 4266, pages 378-388, Kyoto Japan, 2006. Springer. 15. Vı́ctor H. Garcı́a-Pichardo, Raúl Monroy, Maricela Quintana. Web Attack Detection Using ID3. In, John Debenham, editor, Proceedings of the 2nd IFIP International Symposium on Professional Practice on AI, IFIP Vol. 218, pages 323-332, Santiago, Chile, 2006. Springer. 16. Fernando Godı́nez, Dieter Hutter and Raúl Monroy. On the Use of Word Networks to Mimicry Attack Detection. In, G. Müller and G. Schneider, eds., Proceedings of the International Conference on Emerging Trends in Information and Computer Security, ETRICS’06, LNCS Vol. 3995, pages 423-435, Freiburg, Germany, 2006. Springer. 17. L.-A. Dennis, R. Monroy and P. Nogueira. Proof-directed Debugging and Repair. In, H. Nilsson and M. van Eekelen, eds., Proceedings of the Seventh Symposium on Trends in Functional Programming, pages 131-140. 2006. 18. R. Murrieta-Cid, A. Sarmiento, T. Muppirala, S. Hutchinson, R. Monroy, M. Alencastre-Miranda, L. Muñoz-Gómez, R. Swain. A framework for reactive motion and sensing planning: a critical events-based approach. In A. Gelbukh, A. de Albornoz and H. Terashima, Proceedings of the Fourth Mexican International Conference in Artificial Intelligence, MICAI‘05, LNCS Vol. 3789, pages 999-1009, Monterrey, Nuevo León, Mexico, Springer-Verlag. Best Paper Award Recipient. 19. F. Godı́nez, D. Hutter and R. Monroy. On the Role of Information Compaction to Intrusion Detection. In H. Unger, editor, Proceedings of Fifth IEEE International Symposium and School on Advance Distributed Systems ISSADS 2005, LNAI Vol. 3563, pages 83-98, Guadalajara, Jalisco, México, 2005. Springer-Verlag. 20. F. Godı́nez, D. Hutter and R. Monroy. Audit File Reduction Using NGram Models. In A. Patrick and M. Yung, eds., Proceedings of the Ninth International Conference on Financial Cryptography and Data Security, FC‘05, LNCS Vol. 3570, pages 336-341, Roseau, The Commonwealth Of Dominica, 2005. Springer-Verlag. 21. F. Godı́nez, D. Hutter and R. Monroy. Service Discrimination and dit File Reduction for Effective Intrusion Detection. In C.H. Lim M. Yung, eds., Proceedings of the Workshop on Information Security plications, WISA 2005, LNCS Vol. 3325, pages 101-115, Jeju Island, rea, 2005. Springer-Verlag. Auand ApKo- 22. J.C. López and R. Monroy. A Rippling-Based Difference Reduction Technique to Automatically Prove Security Protocol Goals. In C. Lemaı̂tre, C.A. Reyes and J.A. Gonzales, eds., Proceedings of the IX Ibero-American Conference on Artificial Intelligence, IBERAMIA 2004, LNAI Vol. 3315, 18 pages 364-374, Puebla, Mexico, 2004. Springer-Verlag. Candidate to Best Paper Award. 23. Raúl Monroy. A Process Algebra Model of the Immune System. In M.G. Negoita, editor, Proceedings of the 8th Knowledge-Based Intelligent Information & Engineering Systems, KES‘04, LNAI Vol. 3214, pages 526533, Wellington, New Zealand, September 2004. Springer-Verlag. 24. F. Godı́nez, D. Hutter and R. Monroy. Attribute Reduction for Effective Intrusion Detection. In J. Favela, E. Menasalvas, and E. Chávez, eds., Proceedings of the 2004 Atlantic Web Intelligence Conference, AWIC‘04, LNAI Vol. 3034, pages 74-83, Cancún, Mexico, 2004. Springer-Verlag. 25. R. Monroy and M. Carrillo. Automatic Formulation of Security Properties Under the Inductive Approach. In M.H. Hamza, editor, Proceedings of IASTED‘03, Applied Informatics-Software Engineering, pages 1020-1025, Innsbruck, Austria, 2003. Acta Press. 26. M. Carrillo and R. Monroy, Towards Automating the Use of the Inductive Approach for the Verification of Security Protocols. In H. Sossa and G. Arroyo, eds., Proceedings of MICAI/TAINA‘02, avances en inteligencia artificial, pages 125-134, Merida, Mexico, 2002. Centro de Investigación en Computación-IPN, 2002. 27. R. Saab, R. Monroy and F. Godı́nez. Towards a Model for an Immune System. In Coello-Coello, C., de Albornoz, A., Sucar, L.E. and Battistutti, O.C., eds., Proceedings of the 2nd Mexican Internation Conference on Artificial Intelligence, MICAI‘02, LNAI vol. 2313, pages 401-410, Mérida, Mexico, 2002. Springer-Verlag. Best Paper Award Recipient. 28. R. Monroy. Concept Formation via Proof Planning Failure. In R. Nieuwenhuis and A. Voronkov, eds., Proceedings of the 8th International Conference in Logic for Programming, Artificial Intelligence and Reasoning, LPAR‘01, LNAI Vol. 2250, pages 718-731, La Havana Cuba, 2001. Springer-Verlag. 29. M. Carrillo and R. Monroy. Lógicas de autenticación aplicadas al estudio de protocolos. In Proceedings of the 27th Conferencia Latinoamericana en Informática, CLEI‘2001. Mérida, Venezuela, 2001. CLEI. 30. R. Monroy. The use of Abduction and Recursion-Editor Techniques for the Correction of Faulty Conjectures. In P. Flenner and P. Alexander, eds., Proceedings of the 15th Conference on Automated Software Engineering, ASE’00, pages 91-99, Grenoble, Francia, 2000. IEEE Computer Science Press. Candidate to best paper award. 31. E. Navarrete, E. Garcı́a and R. Monroy. Reconocimiento de patrones en la exposición fotográfica. In L.A. Trejo, editor, Proceedings of the 26th Conferencia Latinoamericana de Informática, CLEI 2000, Atizapán, Mexico, 2000. CLEI. 19 32. R. Monroy, A. Bundy, and I. Green. Searching for a Solution to Program Verification = Equation Solving in CCS. In O. Cairó and F. Cantú, eds., Proceedings of the Mexican Internation Conference on Artificial Intelligence, MICAI‘00, LNAI Vol. 1793, pages 1-13, Acapulco, Mexico, 2000. Springer-Verlag. 33. R. Monroy. The Use of Proof Planning Failure for Correcting Faulty Conjectures. In J.M. Ahuactzin, editor, 2nd Mexican Conference in Computer Science, ENC’99, pages 1-6, Pachuca, Mexico, 1999. Sociedad Mexicana de Ciencia de la Computación. 34. R. Monroy. On the Correction of Faulty Formulae. In A. de Albornoz, and M. Alvarado, eds., Taller de Inteligencia Artificial, TAINA‘99, pages 56 - 68, D. F., Mexico, 1999. Instituto Politécnico Nacional. 35. R. Monroy, A. Bundy, and I. Green. Planning Equational Verification in CCS. In D. Redmiles and B. Nuseibeh, eds., Proceedings of the 13th Conference on Automated Software Engineering, ASE‘98, pages 43 - 52, Hawaii, USA, 1998. IEEE Computer Society Press. Candidate to Best Paper Award. 36. R. Monroy, A. Bundy, and I. Green. Annotated Term Rewriting for Deciding Observation Congruence. In H. Prade, editor, Proceedings of the 13th European Conference on Artificial Intelligence, ECAI‘98, pages 393-397, Brighton, England, 1998. Wiley & Sons. 37. R. Monroy. Observant: an Annotated Term Rewriting for Deciding Observation Congruence. In S. Negrete, editor, Encuentro Nacional de Computación, ENC’97, pages 40-50, Querétaro, Mexico, 1997. Universidad Autónoma de Querétaro. 38. R. Monroy, A. Bundy, and A. Ireland. Proof Plans for the Correction of Faulty Conjectures. In F. Pfenning, editor, Proceedings of the 5th International Conference on Logic Programming and Automated Reasoning, LPAR’94, LNAI Vol. 822, pages 54-68, Kiev, Ukraine, 1994. SpringerVerlag. Also available from Edinburgh as Research paper 681. Journal Papers (peer-reviewed) 1. B. Cervantes, M. González-Mendoza, R. Monroy, C.-E. Galdámez-Blanco, E.-I. Garcı́-Pérez. Hacia la construcción de una herramienta para la creación de bitácoras para Android. Journal of Research in Computing 93:111-120, CIC del IPN, 2015. 2. J. Rodrı́guez-Ruiz, R. Monroy and J.-B. Camiña-Prado. Hacia la detección de impostores mediante un modelo basado en tareas. Journal of Research in Computing 62:45-56, CIC del IPN, 2013. Selected as the 3rd best paper of the conference, award granted by the Mexican Society for Artificial Intelligence. 20 3. J.-B. Camiña and R. Monroy. WUIL: una base de datos para probar mecanismos de detección de intrusos. Journal of Research in Computing 62:57-66, CIC del IPN, 2013. 4. R. Alonso, R. Monroy, L. Trejo. Complejidad computacional de un caso especial del cálculo de grupos en las redes de interacción. Research in Computing Science 55(1):138-154, CIC-IPN, 2012. Selected as the 2nd best paper of the conference, award granted by the Mexican Society for Artificial Intelligence. 5. J. Vázquez, R. Monroy and L. Trejo. Un Nuevo Esquema para la Detección de Ataques en Redes Inalámbricas. Research in Computing Science 55(1):297 - 308, CIC, IPN, 2012. 6. B. Camiña, C. Hernández and R. Monroy. Hacia la detección de impostores mediante grafos de navegación. Research in Computing Science 55(1):285 - 296, CIC - IPN, 2012. 7. J. C. López-Pimentel, V. Ramos Fon Bon and R. Monroy. A Web Service for Signing and Authenticating Digital Documents based on Symmetric Cryptography Protocol. International Journal of Digital Information and Wireless Communications (IJDIWC) 1(2): 434-444. The Society of Digital Information and Wireless Communications (SDIWC), 2012. 8. K. A.-Garcı́a-Gamboa, E. Aguirre-Bermudez, R. Monroy and C. MexPerera. Forensic Intrusion Detection on System Logs. In, A. Gelbukh (ed.), Artificial Intelligence and Applications, Sociedad Mexicana de Inteligencia Artificial, pp: 231—241, 2009. 9. R. Alonso-Rodrı́guez, J.Vázquez-Islas, L. A.-Trejo-Rodrı́guez, R. Monroy and E. Sánchez-Velázquez. How Social Networks Can Help to Detect DDoS Attacks on DNS Servers. In, A. Gelbukh (ed.), Artificial Intelligence and Applications, Sociedad Mexicana de Inteligencia Artificial, pp: 261—270, 2009. 10. E. Aguirre-Bermudez, K. A.-Garcı́a-Gamboa and R. Monroy. Coloured Petri Nets for Modelling Host-Based Attacks. In, A. Gelbukh (ed.), Artificial Intelligence and Applications, Sociedad Mexicana de Inteligencia Artificial, pp: 281—290, 2009. 11. Carlos Mex-Perera, José Zamora-Elizondo and Raúl Monroy. Intrusion Detection for Mobile Ad-Hoc Networks Based on a Non-Negative Matrix Factorization. Journal of Research in Computing 40:131-140, CIC del IPN, 2008. 12. M. Alencastre-Miranda, L. Muñoz-Gómez, R. Murrieta and R. Monroy. Local Reference Frames vs. Global Reference Frame for Mobile Robot Localization and Planning. In, A. Gelbukh and C. A. Reyes, eds., Journal of , Mexico, 2006. IEEE Computer Society Press. 21 13. K. Garcı́a, R. Monroy and J. Vázquez. An Artificial Manager for Security Policies in Organizations. Journal of Research in Computing Science. 17:97–106, 2005. 14. A. Calixto and R. Monroy. TLS Analysis Using CADP. Studia Informatica Universalis, 2(2):234-249, 2002. Doctoral External Examining • External examiner, Tecnológico de Monterrey, campus Monterrey, 2015, PhD, Carolina del Valle. • External examiner, Centro de Investigación en Matemáticas, 2015, PhD, Israel Becerra. • External examiner, Centro de Investigación y de Estudios Avanzados del IPN (CINVESTAV), 2015, Lil Marı́a Xibai Rodrı́guez Henrı́quez; • External examiner, Centro de Investigación y de Estudios Avanzados del IPN (CINVESTAV), 2013, Cuauhtemoc Mancillas López; • External examiner, Centro de Investigación en Matemáticas (CIMAT), 2013, PHD, Ubaldo Ruiz López; • External examiner, Universidad Michoacana de San Nicolás Hidalgo, 2011, PhD, Anastacio Antolino Hernández; • External examiner, Tecnológico de Monterrey, campus Monterrey, 2009, PhD, Rafael A. Ayala Rodrı́guez; • External examiner, Tecnológico de Monterrey, campus Monterrey, 2008, PhD, Marcelo Fernández; • External examiner, Tecnológico de Monterrey, campus Monterrey, 2003, PhD, Jaime Solano; and • External examiner, Tecnológico de Monterrey, campus Morelos, 2005, PhD, Juan Segura. MSc External Examining • External examiner, ESIME — Culhuacan, IPN, 2015, MSc, Ilce Belén Ramı́rez Osnaya. • External examiner, Centro de Investigación en Matemáticas, 2010, MSc, Israel Becerra. Book Reviews 1. Long, L. and Long, N. Introducción a las computadoras y a los sistemas de información, 5ta edición, Prentice Hall Hispanoamericana, 1999. 22 Magazine Papers 1. Raúl Monroy. Obituario Tardı́o por Donald Michie. La Jornada de Oriente, Junio 2, 2008. 2. Paralelismo en Computación. Soluciones Avanzadas, Vol. 1, No. 5, pp 4 – 10, Octubre, 1993. Guest Lectures 1. ‘Detección de impostores basada en navegación de archivos’, CINVESTAV, Mayo, 2015. 2. ‘Inteligencia Artificial en la Seguridad Informática’, Universidad Michoacana de San Nicolás Hidalgo, Abril, 2015. 3. ‘Information Flow in Disaster Management Systems’, Intelligent Disaster Management Workshop. February, 2015. 4. ‘A model based on social structures to detect traffic anomalies on DNS servers’, 9th Latin American Workshop on Logic/Languages Algorithms and New Methods of Reasoning 2014 (LANMR‘14). November, 2014. 5. ‘Detección oportuna de impostores y la base de datos WUIL-DS’, Rtronics. Universidad Tecnológica de Tlaxcala. Septiembre 2013. 6. ‘Detección oportuna de impostores y la base de datos WUIL-DS’, Rtronics. Congreso Mexicano de Inteligencia Artificial. Mayo 2013. 7. ‘Detección oportuna de impostores y la base de datos WUIL-DS’, Rtronics. Universidad Autónoma del Estado de México, campus Valle de México. Abril 2013. 8. ‘Detección oportuna de impostores y la base de datos WUIL-DS’, Rtronics. Tecnológico de Monterrey, Campus Estado de México. October 2012. 9. ‘Detección oportuna de impostores y la base de datos WUIL-DS’, Semana ingenierı́a. UNAM, FES Aragón. October 2012. 10. ‘Detección oportuna de impostores y la base de datos WUIL-DS’, II Encuentro internacional en ingenierı́a de sistemas e informática, EIISI‘2012. Universidad Pedagógica y Tecnológica de Colombia. October 2012. 11. ‘Aprovechando la adversidad, descubrimientos en la reparación automática de protocolos’, 2do Congreso nacional de ciencias básicas. Universidad Autónoma Juárez Tabasco. August 2012. 12. ‘Descubrimiento sobre el uso productivo del fracaso al intentar verificar un modelo’, II Encuentro internacional en ingenierı́a de sistemas e informática, EIISI‘2011. Universidad Pedagógica y Tecnológica de Colombia. October 2011. 23 13. ‘Las redes temáticas de investigación del CONACYT’, VI Congreso nacional de investigación. Universidad Pedagógica y Tecnológica de Colombia. Octubre 2011. 14. ‘On Automatically Fixing Security Protocols”, Mexican International Conference on Computer Science, ENC‘2011, SMCC. March 2011; 15. ‘Some Encounters on the Productive Use of a Failed Proof Attempt or a Counterexample”, MICAI‘2010, SMIA. Noviembre 2010; 16. ‘Some Encounters on the Productive Use of a Failed Proof Attempt or a Counterexample”, Semana de la investigación 2010, ITAM. Octubre 2010; 17. ‘Corrección automática de Protocolos de Seguridad’. Seminario de investigación. Instituto de Investigaciones Eléctricas, IIE. Septiembre, 2010; 18. ‘On the Automated Correction of Faulty Security Protocols’, Research Seminar at DFKI, Bremen. June 2010; 19. ‘Corrección automática de Protocolos de Seguridad’. Seminario de investigación. Centro de Investigación en Matemáticas, CIMAT. Mayo 14, 2010; 20. ‘Corrección de Protocolos de Seguridad’. INTROMISIÓN 2008. Facultad de Ciencias de la UNAM. Noviembre 24, 2008; 21. ‘Métodos Formales en el Desarrollo de Software’. 1er Congreso en Inteligencia Artificial y Robótica. Universidad Autónoma de México. Noviembre 21, 2008; 22. ‘La Situación de la Computación en México (Panelista)’. Congreso Celebración de los 25 años de los Posgrados en Computación en el CINVESTAV. CINVESTAV. Septiembre 4, 2008; 23. ‘On the Automated Correction of Security Protocols Susceptible to a Replay Attacks’. Seminario del CINVESTAV. CINVESTAV. Mayo 12, 2008; 24. ‘A complexity result for the Pursuit-Evasion Game of Maintaining Visibility of a Moving Evader’. Segundo Taller de Robótica y Planificación de Movimientos. CIMAT. México. Febrero 2008; 25. ‘México ¿Crecimiento o Estagnación de la Cooperación en Investigación en los Programas Marco de la Comunidad Europea?’. LA-Winds. Diciembre 7, 2007; 26. ‘On the Automated Correction of Security Protocols Susceptible to a Replay Attack’, Seminario Internacional en Sistemas y Computación de la VI Semana Cientı́fica “Ciencia y Vida”, Fundaci’on Universitaria Juan de Castellanos, Tunja, Colombia, Octubre 26, 2007; 24 27. ‘On Patching Faulty Security Protocols’, Scottish Theorem Proving seminar, School of Computer Science at St Andrews University, St Andrews, UK, October 13, 2006; 28. ‘A method for patching interleaving-replay attacks in faulty security protocols’, CISA seminar, Centre for Intelligent Systems and Applications of the School of Informatics at Edinburgh University, Edinburgh, UK, August 31, 2006; 29. ‘On Automatically Patching Faulty Security Protocols, seminario de investigación, Centro de investigación en Matemáticas, CIMAT, Guanajuato, July 6, 2006; 30. ‘Audit File Reduction Using NGram Models’, 36 congreso de investigación y desarrollo del Tecnológico de Monterrey, Monterrey, N.L., 2006; 31. ‘Guı́a para preparar propuestas de investigación y artı́culos de revista’, 36 congreso de investigación y desarrollo del Tecnológico de Monterrey, Monterrey, N.L., 2006; 32. ‘Seguridad Computacional’, Semana de computación de la Universidad Autónoma del Estado de México, Toluca, México, 2005; 33. ‘Errores en el Desarrollo de Sistemas: Amenazas y Soluciones’, Sexto Congreso Estudiantil de Computación, CORE’05 at Centro de Investigación en Computación del Instituto Politécnico Nacional, Mexico City, Mexico, 2005. 34. ‘Predicate Synthesis for the Correction of Faulty Conjectures’, 35 Congreso de Investigación y Desarrollo Tecnológico at ITESM, Monterrey, Mexico, 2005. 35. ‘Lógica Computacional y Agentes Inteligentes’, Tercer Semana Cientı́fica at Fundación Universitaria Juan Castellanos, Tunja, Colombia, 2004. 36. ‘Automated Formulation of Security Goals under the Inductive Approach’, 34 Congreso de Investigación y Desarrollo Tecnológico at ITESM, Monterrey, Mexico, 2004. 37. ‘Modelo Computacional de un Sistema Inmune Humano’, 7o Simposium Internacional de Sistemas y Computación at 18th International Joint Conference on Artificial Intelligence, IJCAI, Acapulco, Mexico, 2003. 38. ‘Aplicaciones de Inteligencia Artificial en Seguridad Computacional’, Tercer Seminario de Seguridad Informática y Tecnologı́as de Información, organised by Secretarı́a de la Defensa Nacional, 2003. 39. ‘Inteligencia Artificial’, Sexta Semana Académica at Tecnológico de Estudios Superiores de Coacalco, Coacalco, Mexico, 2003. 25 40. ‘Towards a Model for an Immune System’, 33 Congreso de Investigación y Desarrollo Tecnológico at ITESM, Monterrey, Mexico, 2003. 41. ‘Uso productivo del fracaso en la búsqueda de una demostración’, seminario de investigación, consorcio interrectorı́as del Tecnológico de Monterrey, Atizapán, Mexico, 2003. 42. ‘Concept Formation Via Proof Planning Failure’, 32 Congreso de Investigación y Desarrollo Tecnológico at ITESM, Monterrey, Mexico, 2002. 43. ‘Técnicas de Automatización en el Razonamiento para el Desarrollo de Sistemas’, Segundo Ciclo de Expoconferencias en Informática y Sistemas Computacionales at Instituto de Educación Superior de Chiapas, Tuxtla Gutiérrez, Mexico, 2001. 44. ‘Análisis de Protocolos de Seguridad’, Ciclo de Conferencias y Seminarios en Seguridad Informática at Universidad Nacional Autónoma de México, Mexico City, Mexico, 2001. 45. ‘The Uses of Abduction and Recursion-Editor Techniques for the Correction of Faulty Conjectures’, 31 Congreso de Investigación y Desarrollo Tecnológico at ITESM, Monterrey, Mexico, 2001. 46. ‘On the Correction of Faulty Conjectures’, Doctoral Research Seminar, Centre for Artificial Intelligence at Tecnológico de Monterrey, Monterrey, Mexico, 2000. 47. ‘Desarrollo de Sistemas Automáticos para la Verificación de Software y Hardware’, Semana de Computación at Universidad Autónoma del Estado de México, Atizapán, Mexico, 2000. 48. ‘Planeación de Verificación de Sistemas Concurrentes’, Octava Semana de Computación at Benemérita Universidad Autónoma de Puebla, Puebla, Mexico, 1999. 49. ‘Corrección de errores en formulaciones incorrectas’, Cómputo 99, Mexico City, Mexico, 1999. 50. ‘Lógica de Autenticación’, Seminario en Seguridad Computacional at Rectorı́a de la Universidad Virtual del Tecnológico de Monterrey, Atizapán, Mexico, 1999. 51. ‘Demostración Automática por Inducción Matemática y sus Aplicaciones’, Ciclo de Conferencias en Inteligencia Artificial at Tecnológico de Monterrey, Atizapán, Mexico, 1999. 52. ‘Por qué y Para qué Estudiar Inteligencia Artificial’, Ciclo de Conferencias en Inteligencia Artificial at Tecnológico de Monterrey, Atizapán, Mexico, 1999. 26 53. ‘Planning Proofs of Equations’, 29 Congreso de Investigación y Desarrollo Tecnológico at ITESM, Monterrey, Mexico, 1999. 54. ‘Verificación Automática de Sistemas de Comunicación’, Taller de Inteligencia Artificial (TAINA’98), Mexico City, Mexico, 1998. 55. ‘Trends in Operating Systems’, United States Trade Center Conference, Mexico City, Mexico, 1991. 56. ‘La Enseñanza en Telecomunicaciones, Mexico y el Mundo: Expectativas y Tecnologı́a en ese Instituto’, III Seminario “Banca y Telecomunicaciones”, organised by Asociación Mexicana de Bancos, Guadalajara, Mexico, 1991. Contexts in which my Work Has Been Cited Type A Citations (194) • B. Tovar, L. Muñoz-Gomez, R. Murrieta-Cid, M. Alencastre-Miranda, R. Monroy and S. Hutchinson. Planning Exploration Strategies for Simultaneous Localization and Mapping. Journal of Robotics and Autonomous Systems 54(4):314-331, 2006. Elsevier. 1. S. Chen, Y. Pisan, and C. Tien-Tan. A Scouting Strategy for RealTime Strategy Games. In Proceedings of the 2014 Conference on Interactive Entertainment. ACM, 2014. 2. F. Amigoni, N. Basilico, A. Q. Li. Moving From ‘How to go There?’to ‘Where to go?’: Towards Increased Autonomy of Mobile Robots. In New Trends in Medical and Service Robots, pp. 345-356, 2014, Springer International Publishing. 3. L. M. Miller, T. D. Murphey. Trajectory optimization for continuous ergodic exploration on the motion group se (2). In Decision and Control (CDC), 2013 IEEE 52nd Annual Conference on, pp. 45174522, 2013, IEEE. 4. A AlDahak, L. Seneviratne, and J. Dias. Frontier-based exploration for unknown environments using incremental triangulation. In Safety, Security, and Rescue Robotics (SSRR), 2013 IEEE International Symposium on, pp. 1-6, 2013, IEEE. 5. H. Yu, Y. Zhang, Y. Wang, and J. Zhu. Fast and robust frontier line segment extracting method based on FCM for robot exploration. In Chinese Automation Congress (CAC), pp. 685-690, 2013, IEEE. 6. F. Amigoni, A. Quattrini-Li, and D. Holz. Evaluating the impact of perception and decision timing on autonomous robotic exploration. In Proceedings of the European Conference on Mobile Robotics, ECMR’2013, pp. 68-73, 2013, IEEE. 27 7. R. Cipolleschi, M. Giusto, A. Quattrini-Li, F. Amigoni. Semantically-informed coordinated multirobot exploration of relevant areas in search and rescue settings. In Proceedings of the European Conference on Mobile Robotics, ECMR’2013, pp. 216-221, 2013, IEEE. 8. F. Amigoni, N. Basilico, and A. Quattrini-Li. How Much Worth Is Coordination of Mobile Robots for Exploration in Search and Rescue? In RoboCup 2012: Robot Soccer World Cup XVI, LNCS Vol. 7500, pp. 106-117, 2013. Springer. 9. T. Wattanavekin, T. Ogata, T. Hara, and J. Ota. Mobile Robot Exploration by Using Environmental Boundary Information. ISRN Robotics, 2013. Hindawi Publishing Corporation. 10. P. Chand and D.A. Carnegie. Mapping and exploration in a hierarchical heterogeneous multi-robot system using limited capability robots. Robotics and Autonomous Systems 61(6):565 - 579, 2013. Elsevier. 11. M. Juliá, A. Gil, O. Reinoso. A comparison of path planning strategies for autonomous exploration and mapping of unknown environments. Autonomous Robots 33(4):427-444, 2012. Springer. 12. A. Parulkar, P. Shukla, K. and M. Krishna. Fast randomized planner for SLAM automation. In 2012 IEEE International Conference on Automation Science and Engineering, CASE 2012, pages 765-770, 2012. IEEE Computer Science Press. 13. I. Jebari, S. Bazeille, and D. Filliat. Combined Vision and FrontierBased Exploration Strategies for Semantic Mapping. In Informatics in Control, Automation and Robotics, 2012. LNEE, Vol. 133, Part 1, pages 237-244, 2012. Springer. 14. A. Quattrini-Li, F. Amigoni, N. Basilico: Searching for Optimal OffLine Exploration Paths in Grid Environments for a Robot with Limited Visibility. In, J. Hoffmann, B. Selman, editors, Proceedings of the Twenty-Sixth AAAI Conference on Artificial Intelligence, AAAI Press 2012 15. A. Quattrini-Li. Development of a framework for evaluating performance of exploration strategies of autonomous robots. Unpublished PhD thesis. Politecnico de Milano. 2011. 16. QUN, Z. Path Planning, Mapping and Learning for Mobile Robot Navigation, Doctoral dissertation, NATIONAL UNIVERSITY OF SINGAPORE, 2012. 17. E. Mattison, and K. Ghose. Towards an Autonomous Indoor Vehicle: Utilizing a Vision-Based Approach to Navigation in an Indoor Environment. In IT Convergence and Services, LNEE, Vol. 107, Part 4, pages 367-375, 2011. Springer. 28 18. P. M.-Walker, A. Kolling, and M. Lewis: Human exploration patterns in unknown, time-sensitive environments. In Proceedings of the IEEE International Conference on Systems, Man and Cybernetics, SMC 2011, pages 2870-2876, 2011. IEEE Computer Science Press. 19. P. Chand. Development of an Artificial Intelligence System for the Instruction and Control of Cooperating Mobile Robots. Unpublished PhD thesis. University of Victoria. 2011 20. Walcott, Aisha. Long-term robot mapping in dynamic environments. Unpublished PhD thesis. Massachusetts Institute of Technology. 2011. 21. D. Holz, N. Basilico, and F. Amigoni. A comparative evaluation of exploration strategies and heuristics to improve them. In European Conference on Mobile Robots, October 2011. 22. N. Basilico and F. Amigoni. Exploration strategies based on multicriteria decision making for searching environments in rescue operations. Autonomous Robots 31(4):401-417, 2011. Springer. 23. N. Basilico and F. Amigoni. Exploration strategies based on MultiCriteria Decision Making for search and rescue autonomous robots. In Tumer, Yolum, Sonenberg and Stoneeds, editors, Proc. of 10th Int. Conf. on Autonomous Agents and Multiagent Systems (AAMAS 2011), pp. 99-106, 2011. IFAAMAS. 24. N. Basilico and F. Amigoni. Defining effective exploration strategies for search and rescue applications with Multi-Criteria Decision Making. In Proceedings of the 2011 International Conference on Robotics and Automation, ICRA’2011, pages 4260 - 4265, 2011, IEEE Computer Science Press. 25. V. Bhatawadekar, D. Fehr, V. Morellas, N. Papanikolopoulos. A dynamic sensor placement algorithm for dense sampling. In Proceedings of the 14th International Conference on Information Fusion FUSION’2011, pages 1 - 7, 2011, IEEE Computer Science Press. 26. X. Zhang, Y. Sun, J. Xiao, and F. Cabrera-Mora. Theseus gradient guide: An indoor transmitter searching approach using received signal strength. In Proceedings of the 2011 International Conference on Robotics and Automation, ICRA’2011, pages 2560 - 2565, 2011, IEEE Computer Science Press. 27. S.-S. Ge, Q. Zhang, A.-T. Abraham, B. Rebsamen. Simultaneous Path Planning and Topological Mapping (SP2ATM) for environment exploration and goal oriented navigation. Robotics and Autonomous Systems 59(3-4): 228-242, 2011. 28. I. Jebari, S. Bazeille, E. Battesti, H. Tekaya, T. Klein, M.-A. Filliat, D. Meyer, C. Sio-Hoi Ieng, R. Benosman, E. Cizeron, J.-C. Mamanna, B. Pothier. Multi-sensor semantic mapping and exploration 29 of indoor environments. In Proceedings of the 2011 IEEE International Conference on Technologies for Practical Robot Applications, TePRA, pages 151 - 156, 2011, IEEE Computer Science Press. 29. M. Desnoyer, What You See Is What You Get so Look At What You Want To See. Unpublished PhD thesis. School of Computer Science. Carnegie Mellon University. 2011. 30. E. Mattison, and A. Garcia. An autonomous ground explorer utilizing a vision-based approach to indoor navigation. In Robotics Symposium, 2011 IEEE IX Latin American and IEEE Colombian Conference on Automatic Control and Industry Applications (LARC), pages 1-6, 2011. IEEE Computer Society Press. 31. F. Amigoni and N. Basilico. A Decision-Theoretic Framework to Select Effective Observation Locations in Robotic Search and Rescue Scenarios. In Proceedings of the IEEE International Conference on Robtics and Automation (ICRA’2010) Workshop on Search and Pursuit/Evasion in the Physical World. 32. M. Juliá, O. Reinoso, A. Gil, M. Ballesta, L. Payá: A hybrid solution to the multi-robot integrated exploration problem. Engineering Applications of AI 23(4): 473-486, 2010. 33. F. Amigoni and V. Caglioti. An Information-Based Exploration Strategy for Environment Mapping with Mobile Robots. Robotics and Autonomous Systems 58(5):684-699, 2010. Elsevier. 34. A. Duffa and P.F.M.J. Verschure. Unifying perceptual and behavioral learning with a correlative subspace learning rule. Neurocomputing 73(10-12):1810-1830. June, 2010. Elsevier. 35. R. J.-Duro, M. Graña, and J. de Lope. On the potential contributions of hybrid intelligent approaches to Multicomponent Robotic System development. Information Sciences 180(14):2635-2648. July 15, 2010. 36. J.-A. Hernandez, A. Pustowka, E.-F. Caicedo, E.-B. Bacca. Formation control of cooperative robots with limited sensing using a virtual robot as reference. In Proceedings of the 6th Latin American Robotics Symposium (LARS), pages 1-7, 2009. 37. N. Basilico, F. Amigoni. Exploration Strategies based on MultiCriteria Decision Making for an Autonomous Mobile Robot. Proceedings of the Fourth European Conference on Mobile Robots (ECMR2009), pages 259-264, 2009. 38. J. Molina-Vargas, C. Torres-Pinzón, C. Restrepo-Patiño. Técnicas de Inteligencia Artificial para la Solución de Laberintos de Estructura Desconocida. Scientia Et Technica 14(39):135-140, Universidad Tecnológica de Pereira, 2008. 39. N. Kwak, G.-W. Kim, S.-H. Ji, and B.-H. Lee. A Mobile Robot Exploration Strategy with Low Cost Sonar and Tungsten-Halogen 30 Structured Light. Journal of Intelligent and Robotic Systems 51(1):89-111, Springer, 2008. 40. L. Liu, T. G.-Crowe, J. N.-Bakambu. Efficient Exploration Algorithms for Rough Terrain Modeling Using Triangular Mesh Maps. RAM 2008, pages 1206-1211, 2008. IEEE Computer Science Press. 41. Y. Sun, J. Xiao, X. Li, F. Cabrera-Mora. Adaptive Source Localization by a Mobile Robot Using Signal Power Gradient in Sensor Networks. GLOBECOM 2008, pages 17-21, 2008. IEEE Computer Science Press. 42. Francesco Amigoni. Experimental Evaluation of Some Exploration Strategies for Mobile Robots. In Proceedings of the 2008 IEEE International Conference on Robotics and Automation, ICRA 2008, pages 2818-2823, Pasadena, CA, USA, May 19-23, 2008. IEEE Computer Science Press. 43. K. Sridharan, P.-R. Kumar. Robotic Exploration and Landmark Determination: Hardware-Efficient Algorithms and FPGA Implementations. Springer, 2008. 44. B. Lavis, T. Furukawa and H.-F. Durrant-Whyte. Dynamic space reconfiguration for Bayesian search and tracking with moving targets. Autonomous Robots 24(4): 387-399 (2008). Springer. 45. N. Petrellis, F. Gioulekas, M. Birbas, J. Kikidis, and A. Birbas. Application of Forward Error Correcting Algorithms to Positioning Systems. In, Peng-Yeng Yin, editor, Pattern Recognition Techniques, Technology and Applications, pages 591-612, 2008. I-Tech. 46. A. S.-S. Huwedi. 3D Mapping of an Unknown Environment with a Robust Cooperation Team of Mobile Robots. Unpublished PhD thesis. Universität Karlsruhe (Technische Hochschule). 2008. 47. K.-R. Beevers. Mapping with Limited Sensing. PhD Thesis. Rensselaer Polytechnic Institute. New York, USA, 2007. 48. Z. Wei, G. Huang and P. Wang. The Research on Multi-robot Simultaneous Localization Mapping Algorithm. Proceedings of the 2007 IEEE International Conference on Automation and Logistics, pages 1241-1246, 2007. IEEE COmputer Science Press. 49. N. Petrellis, N. Konofaos, and G.-P. Alexiou. Using future position restriction rules for stabilizing the results of a noise-sensitive indoor localization system. Optical Engineering 46(6):1-15, 2007. 50. N. Petrellis, N. Konofaos, and G.-P. Alexiou. A Sensors System for Indoor Localisation of a Moving Target Based on Infrared Pattern Recognition. In, R. Stolkin, editor, Scene Reconstruction Pose Estimation and Tracking, pages 283-304, 2007. I-Tech. 51. B. Lavis, T. Furukawa, H. F.-Durrant-Whyte. Spatially Adaptive Exploration for Autonomous Bayesian Search and Tracking. Submitted to Autonomous Robots, 2007. 31 52. B. Dimitris. Smart Technologies for Environmental Safety and Knowledge Enhancement in Intermodal Transport. In Proceedings of the 46th Conference of the European Regional Science Association, ERSA’06, pages 1-16, Greece, 2006. • R. Murrieta-Cid, R. Monroy, S. Hutchinson and J.-P. Laumond. A complexity result for the Pursuit-Evasion Game of Maintaining Visibility of a Moving Evader. In Proceedings of the 2008 IEEE International Conference on Robotics and Automation, ICRA’08, pages pages 2657-2664, USA, 2008. IEEE Computer Society Press. 1. F Shkurti, and G Dudek. On the complexity of searching for an evader with a faster pursuer. In Proceedings of IEEE International Conference on Robotics and Automation, ICRA’14, pages 4062-4067, 2014, IEEE Computer Science Press. 2. A. Kumar and A. Ojha. Anticipated Velocity Based Guidance Strategy for Wheeled Mobile Evaders Amidst Moving Obstacles in Bounded Environment. In ICT and Critical Infrastructure: Proceedings of the 48th Annual Convention of Computer Society of IndiaVol I Advances in Intelligent Systems and Computing Volume 248, pp 789-798, 2014, Springer. 3. D. J. Kwak and H. J. Kim. Policy Improvements for Probabilistic Pursuit-Evasion Game. Journal of Intelligent and Robotic Systems, 74(3-4):709-724, 2014. Springer. 4. C. Robin and S. Lacroix (2013). Failure anticipation in pursuitevasion. Robotics, 361. 5. Z. Cao, C. Zhou, L. Cheng, Y. Yang, W. Zhang, and M. Tan. A Distributed Hunting Approach for Multiple Autonomous Robots. International Journal of Advanced Robotic Systems 10:217-225, 2013. Intechopen. 6. A. Abdelkader and H. El-Alfy. Visibility Induction for Discretized Pursuit-Evasion Games. In Proceedings of the Twenty-Sixth AAAI Conference on Artificial Intelligence, pages 1976-1982, 2012, AAAI Press. 7. H. El-Alfy. A new approach for the two-player pursuit-evasion game. In Proceedings of the 8th International Conference on Ubiquitous Robots and Ambient Intelligence, URAI’2011, pages 396 - 397, 2011, IEEE Computer Science Press. 8. J. Thunberg, P. Ogren, and X. Hu. A boolean control network approach to pursuit evasion problems in polygonal environments. In Proceedings of the 2011 International Conference on Robotics and Automation, ICRA’2011, pages 4506 - 4511, 2011, IEEE Computer Science Press. 32 9. E. Stump, N. Michael, V. Kumar, V. Isler. Visibility-based deployment of robot formations for communication maintenance. In Proceedings of the 2011 International Conference on Robotics and Automation, ICRA’2011, pages 4498 - 4505, 2011, IEEE Computer Science Press. 10. E. A. Stump and B. M. Sadler. Persistent lance using mutually-visible robotic formations, http://dx.doi.org/10.1117/12.851148, 2011. surveilSPIE : 11. I. Al-Bluwi, A. Elnagar. Maintaining visibility of a moving target: Maximizing escape time vs. exposure time. In Proceedings of the 11th International Conference on Control, Automation, Robotics and Vision, ICARCV 2010, pages 982-987, 2010, IEEE Computer Science Press. 12. C. Giovannangeli, M. Heymann and E. Rivlin. Pursiut-Evasion Games in Presence of Obstacles in Unknown Environments: towards an Optimal Pursuit Strategy. Chaper 4, in Cutting Edge Robotics 2010, pages 47-80, 2010, Intech. 13. I. Al-Bluwi and A. Elnagar. Pursuit Evasion in Dynamic Environments with Visibility Constraints. In, H. Liu, H. Ding, Z. Xiong, and X. Zhu, editors, Proceedings of the Intelligent Robotics and Applications Lecture Notes in Computer Science, 6425:116-129, 2010, Springer. 14. I. Al-Bluwi, A. Elnagar. Maintaining visibility of a moving target: Maximizing escape time vs. exposure time. In Proceedings of the 2010 11th International Conference on Control Automation Robotics Vision ICARCV’2010, pages 982 - 987, 2010, IEEE Computer Science Press. 15. S. Bhattacharya. Pursuit-evasion games in mobile networks. Unpublished PhD Thesis. Electrical and Computer Department. University of Illinois at Urbana-Champaign, 2010. 16. Cheng Wu. Novel function approximation techniques for large-scale reinforcement learning. Unpublished PhD Thesis. College of Engineering, Department of Electrical and Computer Engineering at Northeastern University, 2010. 17. H. El-Alfy, D. Jacobs and L. Davis. Assigning Cameras to Subjects in Video Surveillance Systems. In Proceedings of the IEEE International Conference on Robotics and Automation, ICRA’09, pages 837-843, Kobe, Japan, May 12-17, 2009. IEEE Computer Science Press. 18. H.-M. El-Alfy. Techniques For Video Surveillance: Automatic Video Editing And Target Tracking. Unpublished PhD Thesis. University of Maryland. 2009. 33 19. E.-A. Stump. Control for Localization and Visibility Maintenance of an Independent Agent using Robotic Teams. Unpublished PhD Thesis. University of Pennsylvania, 2009. 20. Christophe Giovannangeli. Pursuit-evasion games in presence of obstacles. Reseach report MRTN-CT-2004-005439. Sixth Framework Programme. 2009. • Vı́ctor H. Garcı́a-Pichardo, Raúl Monroy, Maricela Quintana. Web Attack Detection Using ID3. In, John Debenham, editor, Proceedings of the 2nd IFIP International Symposium on Professional Practice on AI, IFIP Vol. 218, pages 323-332, Santiago, Chile, 2006. Springer. 1. K. Goseva-Popstojanova, G. Anastasovski, A. Dimitrijevikj, R. Pantev, and B. Miller. Characterization and classification of malicious Web traffic. Computers and Security, 42:92-115. 2014. 2. C. I. Pinzón, J. F. de Paz, Á. Herrero, E. Corchado, J. Bajo, J. M. Corchado. idMAS-SQL: Intrusion Detection Based on MAS to Detect and Block SQL injection through data mining. Information Sciences, 2013. Elsevier. http://dx.doi.org/10.1016/j.ins.2011.06.020. 3. S. K. Pramanik, S. Pramanik, B. K. Pramanik, M. K. Islam-Molla and Md. E. Hamid. Hybrid Classification Algorithm for Knowledge Acquisition of Biomedical Data. International Journal of Advanced Science and Technology 44:99-112, July, 2012. 4. S. Jaiswal, N. Gupta, H. Shrivastava. Enhancing the features of Intrusion Detection System by using machine learning approaches. International Journal of Scientific and Research Publications, 2(2):166170, 2012. 5. A. S. Issa. Intrusion Detection System Based on Decision Tree and Clustered Continuous Inputs. Raf. J. of Comp. & Math’s. 8(1):7987, 2011. 6. A.-M. Brifcani and A.-S. Issa. Intrusion Detection and Attack Classifier Based on Three Techniques: A Comparative Study. Eng. and Tech. Journal, 29(2):396-412, 2011. 7. S.-A. Talekar, V.-S. Tidake, and P.-V. Shinde. Intelligent network sniffer: a data mining approach. In Proceedings of the International Conference and Workshop on Emerging Trends in Technology, ICWET’11, pages 258 - 261, 2011. ACM. 8. H. Sarvari, M Mehdi-Keikha. Improving the accuracy of intrusion detection systems by using the combination of machine learning approaches. In Proceedings of the Second International Conference of Soft Computing and Pattern Recognition, SoCPaR 2010, pages 334337, 2010. IEEE Computer Science Press. 34 9. C. Pinzón, J.-F. de Paz, J. Bajo, A. Herrero, and E. Corchado. AIIDA-SQL: An Adaptive Intelligent Intrusion Detector Agent for detecting SQL Injection attacks. In Proceedings of the 10th International Conference on Hybrid Intelligent Systems (HIS’2010), pages 73 - 78, 2010. IEEE Computer Science Press. 10. C. Pinzón, A. Herrero, J. F.-de Paz, E. Corchado and J. Bajo. CBRid4SQL: A CBR Intrusion Detector for SQL Injection Attacks. HAIS 2010, Part II, LNAI 6077:510-519, 2010. Springer. 11. J. Bajo, J.-M. Corchado, C. Pinzón, Y. de Paz, B. Pérez-Lancho. SCMAS: A Distributed Hierarchical Multi-Agent Architecture for Blocking Attacks to Databases. International Journal of Innovative Computing, Information and Control 6(4)1:10, April 2010; 12. C. Pinzón. Arquitectura multi-agente adaptativa para la deteccin de ataques en entornos dinmicos y distribuidos. Unpublished PhD Thesis. Universidad de Salamanca, 2010. 13. Gregory Blanc and Youki Kadobayashi. Towards Learning Intentions in Web 2.0. In D.-J. Guan, editor, Proceedings of the 2009 Joint Workshop on Information Security, August 6-7, 2009, Taiwan, 2009. 14. Liang Guangmin. Modeling Unknown Web Attacks in Network Anomaly Detection. In Proceedings of the 2008 Third International Conference on Convergence and Hybrid Information Technology, Volume 02, pages 112-116. 2008. IEEE Computer Science Press. 15. Lee, Joong-Hee Lee, Jong-Hyouk Sohn, Seon-Gyoung Ryu, Jong-Ho Chung, Tai-Myoung. Effective Value of Decision Tree with KDD 99 Intrusion Detection Datasets for Intrusion Detection System. In Proceedings of 10th International Conference on Advanced Communication Technology, 2008. ICACT 2008, Vol. 2, pages 1170-1175, Gangwon-Do, South Korea, 2008. IEEE Computer Science Press. 16. Zeng Jin-quan, Zhao Hui,Lili Cai-ming,PENG Ling-xi. Principles Inspired Approach to Detection of Web Attacks. Journal of University of Electronic Science and Technology of China 366:1215-1218, December 2007. ISSN 1001-0548 17. Fady Hamoui. Détection de fraudes et Extraction de Connaissances. Unpublished MSc. Université Montpellier II. 2007. • R. Monroy, A. Bundy, and A. Ireland. Proof Plans for the Correction of Faulty Conjectures. In F. Pfenning, editor, Proceedings of the 5th International Conference on Logic Programming and Automated Reasoning, LPAR’94, LNAI Vol. 822, pages 65-68, Kiev, Ukraine, 1994. SpringerVerlag. Also available from Edinburgh as Research paper 681. 1. Moussa Demba. Specialization of Recursive Predicates from Positive Examples Only. Journal of Computer Science 6(6): 619-625, 2010. 35 2. G. Sutcliffe. The SZS Ontologies for Automated Reasoning Software. In, Rudnicki P, Sutcliffe G., Konev B., Schmidt R., Schulz S., eds., Proceedings of the Combined KEAPPA - IWIL Workshops., pp. 3849, Qatar, 2008; 3. Bernhard Gramlich. Strategic Issues, Problems and Challenges in Inductive Theorem Proving. Electronic Notes in Theoretical Computer Science 125(2): 5-43 (2005); 4. M. Demba, F. Alexandre, and K. Bsaı̈es. Correction of faulty conjectures and programs extraction. In, W. Ahrendt, P. Baumgartner and H. de Neville, eds., Proceedings of the CADE-20 Workshop on Disproving-Non-Theorems, Non-Validity, Non-Provability pages 1727, Tallinn, Estonia, 2005. 5. S. Colton and A. Pease. Lakatos-Style Methods in Automated Reasoning. In 16th Eureopean Conference on Artificial Intelligence, ECAI’2004, pp. 977-978, The Netherlands, 2004; 6. F. Alexandre, K. Bsaı̈es, M. Demba. Predicate Synthesis from Inductive Proof Attempt of Faulty Conjectures. Lecture Notes in Computer Science, Vol. 3018, Germany, pp. 20-33, 2003; 7. W. Ahrendt. Deduktive Fehlersuche in Abstrakten Datentypen, Germany, PhD Thesis, 2002; 8. W. Ahrendt. Deductive Search for Errors in Free Data Type Specifications Using Model Generation, Lecture Notes in Computer Science, pp. 211-225, Vol. 2392, Germany, 2002; 9. D. Galmiche. Proof Plans and Proof Nets in Mixed Linear Logic, in Electronic Notes in Theoretical Computer Science, Vol. 37, The Netherlands, 2000; 10. J. Richardson. Proof Planning with Program Schemas, Lecture Notes in Computer Science, pp. 313-315, Vol. 1559, Germany, 1998; 11. M. Protzen. Patching Faulty Conjectures. In, M.-A. McRobbie, J.K. Slaney, eds., Proceedings of the 13th International Conference on Automated Deduction, Lecture Notes in Computer Science vol. 1104, pages 77-91, Springer, 1996; 12. M. Protzen. Disproving Conjectures and Lazy Generation of Induction Hypotheses, Technical University of Darmstad, PhD Thesis, 1995; 13. P. Flener and L. Popelinsky. On the Use of Inductive Reasoning in Program Synthesis: Prejudice Prospects, Lecture Notes in Computer Science, pp. 69-87, Vol. 883, Germany, 1994. • R. Posadas, C. Mex-Perera, R. Monroy and J. A. Nolazco. Hybrid Method for Detecting Masqueraders Using Session Folding and Hidden Markov Models. In, A. Gelbukh and C. A. Reyes, eds., Proceedings of the 5th Mexican International Conference on AI, MICAI 2006, LNAI Vol. 4293, pages 622-631, Mexico, 2006. Springer. 36 1. J. A Iglesias, A. Ledezma, and A. Sanchis. Evolving classification of UNIX users’ behaviors. Evolving Systems, 1-8, 2014, Springer. 2. H. A. Kholidy, F. Baiardi, S. Hariri. DDSGA: A Data-Driven Semi-Global Alignment Approach for Detecting Masquerade Attacks. IEEE Transactions on Dependable and Secure Computing P(99):114, 2014, IEEE. 3. J. E. Tapiador, J. C. Hernandez-Castro and P. Peris-Lopez. Online Randomization Strategies to Obfuscate User Behavioral Patterns. Journal of Network and Systems Management 20(4):561-578, 2012. Springer. 4. H. A. Kholidy and F. Baiardi. CIDD: A Cloud Intrusion Detection Dataset for Cloud Computing and Masquerade Attacks. In Information Technology: New Generations (ITNG) pages 397 - 402, 2012. IEEE Computer Science Press. 5. J. E. Tapiador and J. A. Clark. Masquerade mimicry attack detection: A randomised approach. Computers and Security 30(5):297310, 2011. Elsevier. 6. L. Huang, and M. Stamp. Masquerade detection using profile hidden Markov models. Computers and Security, 30(8):732-747, 2011, Elsevier. doi:10.1016/j.cose.2011.08.003. 7. J.E. Tapiador, J.A. Clark. Masquerade mimicry attack detection: A randomised approach. Computers and Security 30(5):297-310, 2011. 8. A. M. Bartkowiak. Command and Block Profiles for Legitimate Users of a Computer Network. Computer Information Systems — Analysis and Technologies Communications in Computer and Information Science 245:295-304, 2011. Springer. 9. J.E. Tapiador, J.A. Clark. Information-Theoretic Detection of Mimicry Masquerade Attacks, In Proceedings NSS 2010, pages 183 190, 2010. IEEE Computer Society Press. 10. C. Strasburg, S. Krishnan, K. Dorman, S. Basu, J.-S. Wong. Masquerade Detection in Network Environments. In 2010 10th IEEE/IPSJ International Symposium on Applications and the Internet, pages 38-44, 2010. 11. C. Benitez and P. Fierens. Experiments in command dimension reduction in masquerader detection. In Proceedings of V Congreso Iberoamericano de Seguridad Informática, pages 31-45, Montevideo, Uruguay. Universidad de la República de Uruguay, 2008. ISBN: 978-9974-0-0593-8. 12. M. Bertacchini and P. Fierens. A Survey on Masquerader Detection Approaches. In Proceedings of V Congreso Iberoamericano de Seguridad Informática, pages 46-60, Montevideo, Uruguay. Universidad de la República de Uruguay, 2008. ISBN: 978-9974-0-0593-8. 37 • L.-A. Dennis, R. Monroy and P. Nogueira. Proof-directed Debugging and Repair. In, H. Nilsson and M. van Eekelen, eds., Proceedings of the Seventh Symposium on Trends in Functional Programming, pages 131-140. 2006. 1. R. Samanta. Program reliability through algorithmic design and analysis. Unpublished PhD thesis. University of Texas. 2013 2. Andrea Arcuria. Evolutionary repair of faulty software. Applied Soft Computing 11(4): 3494-3514, 2011. 3. H. A. Hussein, K. M. Mahar, M. F. Hussein and O. M. Badawy. Automatic Correction of Programming Faults using Semantic Networks. Acta Press. 10.2316/P.2011.758-034. 4. Andrea, Arcuri. Automatic software generation and improvement through search based techniques. Unpublished PhD thesis. University of Birmingham. 2009. 5. Andrea Arcuri. Evolutionary Repair of Faulty Software. Technical report, CSR-09-02. University of Birmingham, 2009. 6. R. Samanta, J. Deshmukh. and E.-A. Emerson. Automatic Generation of Local Repairs for Boolean Programs. In Formal Methods in Computer-Aided Design, pp. 1-10, 2008. 7. Y. Zhang and Y. Ding. CTL Model Update for System Modifications. Journal of Artificial Intelligence Research 31: 113-155, 2008. 8. J.-S. Fitzgerald and P.-G. Larsen. Balancing Insight and Effort: The Industrial Uptake of Formal Methods. In, C.-B. Jones, Z. Liu and J. Woodcock, eds., Formal Methods and Hybrid Real-Time Systems, Essays in Honor of Dines Björner and Chaochen Zhou on the Occasion of Their 70th Birthdays, LNCS Vol. 4700, pages 237-254, Macao, China, 2007. Springer. • Raúl Monroy. Predicate Synthesis for Correcting Faulty Conjectures: the Proof Planning Paradigm, Automated Software Engineering, an International Journal, (10):247-269, 2003. 1. Alan Bundy. Cooperating Reasoning Processes: More than just the Sum of their Parts. In Proceedings of IJCAI’2007, pp. 2-11, Morgan Kaufmann, 2007. 2. L. A. Dennis. Program Slicing and Middle-Out Reasoning for Error Location and Repair. IJCAR 2006 workshop on Disproving: NonTheorems, Non-Validity and Non-Provability, Seattle, Washington, 2006. 3. J. Souquiére. Demande d’opération QSL Modélisation formelle MODFORM. Project description, QSL (France), 2006; 4. Louise A. Dennis and Pablo Nogueira. What can be Learned from Failed Proofs of Non-Theorems? In Proceedings of the Emerging Trends track of TPHOLs 2005. Technical Report. Oxford University, 2005. 38 5. G. Steel. The Importance of Non-theorems and Counterexamples in Program Verification. In T. Hoare and J. Misra, eds., Proceedings of the Verified Software: Theories, Tools, Experiments (VSTTE) Conference. Position paper, 2005; 6. L. Dennis, The Use of Proof Planning Critics to Diagnose Errors in the Base Cases of Recursive Programs, in 2nd International Joint Conference On Automated Reasoning, pp. (To appear in Electronic Notes in Theoretical Computer Science), 2004. 7. G. Steel, Discovering Attacks on Security Protocols by Refuting Incorrect Inductive Conjectures, PhD Thesis, Edinburgh University, 2003. • J.C.-López P. and R. Monroy. Formal Support to Security Protocol Development: a Survey. Computación y Sistemas, special volume celebrating 50 years of Computing in Mexico, 12(1):89-109, CIC del IPN, 2008. 1. R. Merkel, C. Kraetzer, R. Altschaffel, E. Clausing, M. Schott and J. Dittmann. Fingerprint Forensics Application Protocol: Semiautomated Modeling and Verification of Watermark-Based Communication Using CASPER and FDR. In Digital Forensics and Watermarking LNCS 7128:321-335, 2012. Springer. 2. I. You, Y. Hori, and K. Sakurai. Towards formal analysis of wireless LAN security with MIS protocol. International Journal of Ad Hoc and Ubiquitous Computing 7(2):112 - 120, 2011. InderScience Publishers. 3. C. Kraetzer, R. Merkel, R. Altschaffel, E. Clausing, J. Dittmann. Semi-automated communication protocol security verification for watermarking - pros and cons illustrated on a complex application scenario. In Proceedings of the thirteenth ACM multimedia workshop on Multimedia and security, MM&Sec’11, pages 93-102, 2011. ACM Press. 4. R. Patel, B. Borisaniya, A. Patel, D. Patel, M. Rajarajan, A. Zisman. Comparative Analysis of Formal Model Checking Tools for Security Protocol Verification. In Proceedings of the Third International Conference on Recent Trends in Network Security and Applications, CNSA 2010, Communications in Computer and Information Science 89:152-163, 2010. Springer. 5. N. Moebius, K. Stenzel, W. Reif. Pitfalls in Formal Reasoning about Security Protocols. In Proceedings of ARES 2010 - Fifth International Conference on Availability, Reliability and Security, pages (to appear), 2009, IEEE Computer Science Press. 6. N. Moebius, K. Stenzel, and W. Reif. Formal Verification of Application-Specific Security Properties in a Model-Driven Approach. In, F. Massacci, D.-S. Wallach, N. Zannone, eds., Proceedings of Engineering Secure Software and Systems, Second International 39 Symposium, ESSoS 2010, Pisa, Italy. Lecture Notes in Computer Science Vol. 5965, pages 166-181. Springer-Verlag, 2010. • Juan C. López P., Raúl Monroy and Dieter Hutter. A method for patching interleaving-replay attacks in faulty security protocols. Electronic Notes in Theoretical Computer Science 174(4):117-130, 2007. 1. B. Bonakdarpour, R. Hajisheykhi, and S. S Kulkarni. KnowledgeBased Automated Repair of Authentication Protocols. In Formal Methods FM 2014, pp. 132-147, 2014. Springer International Publishing. 2. A. Jurcut, T. Coffey, R. Dojen. Symmetry in Security Protocol Cryptographic Messages — A Serious Weakness Exploitable by Parallel Session Attacks. In Proceedings of the Seventh International Conference on Availability, Reliability and Security (ARES), 2012, pages 410 - 416, IEEE Computer Society Press, 2012. 3. A. Singhal, P. Rustagi. A Study on Protocol Patching Using SHRIMP. B. Tech Project Report, DA-IICT, Gandhinagar, 2010. 4. M. Jain. Is the attack valid? A tool for detecting erroneous attacks found by Scyther. Dhirubhai Ambani Institute of Information and Communication. B. Tech Project Report, DA-IICT, Gandhinagar, 2008. 5. S. Lal. A Connector between Scyther and SHRIMP. Dhirubhai Ambani Institute of Information and Communication. B. Tech Project Report, DA-IICT, Gandhinagar, 2008. 6. A. Chakaborty. Automated Detection of Typing Flaws. Dhirubhai Ambani Institute of Information and Communication. B. Tech Project Report, DA-IICT, Gandhinagar, 2007. • F. Godı́nez, D. Hutter and R. Monroy. Attribute Reduction for Effective Intrusion Detection. In J. Favela, E. Menasalvas, and E. Chávez, eds., Proceedings of the 2004 Atlantic Web Intelligence Conference, AWIC‘04, LNAI Vol. 3034, pages 74-83, Cancún, Mexico, 2004. Springer-Verlag. 1. N. Senan. Feature selection for traditional Malay musical instrument sound classification using rough set. Unpublished PhD thesis, Universiti Tun Hussein Onn Malaysia. 2013 2. S.-K. Shrivastava, and P. Jain. Effective Anomaly based Intrusion Detection using Rough Set Theory and Support Vector Machine. International Journal of Computer Applications 18(3):35-41, 2011. 3. Neveen I. Ghali. Feature Selection for Effective Anomaly-Based Intrusion Detection. IJCSNS International Journal of Computer Science and Network Security 9(3):285-289, 2009. 4. W. Chimphlee, A.-H. Abdullah, M.-N. Md Sap, S. Chimphlee and S. Srinoy. A Rough-Fuzzy Hybrid Algorithm for Computer Intrusion 40 Detection. The Int. Arab Journal of Inf. Technology 4(3):247-254, 2007. 5. W. Chimphlee, A.-H. Abdullah, M.-N. Md Sap, S. Chimphlee and S. Srinoy. Unsupervised Clustering Methods for Identifying Rare Events in Anomaly Detection. Transactions on Engineering, Computing and Technology 8:253-258, 2005. 6. W. Chimphlee, M.-Noor.M. Sap, A.-H. Abdullah, S. Chimphlee, S. Srinoy. Hybrid Model for Computer Intrusion Detection. Proceedings of the 4th WSEAS Int. Conf. on Information Security, Communications and Computers, Tenerife, Spain, December 16-18, 2005 (pp316-320). • R. Monroy. The use of Abduction and Recursion-Editor Techniques for the Correction of Faulty Conjectures. In P. Flenner and P. Alexander, eds., Proceedings of the 15th Conference on Automated Software Engineering, ASE’00, pages 91-99, Grenoble, Francia, 2000. IEEE Computer Science Press. 1. Moussa Demba. Specialization of Recursive Predicates from Positive Examples Only. Journal of Computer Science 6(5): 512-518, 2010. 2. M. Demba, F. Alexandre, and K. Bsaı̈es. Correction of faulty conjectures and programs extraction. In, W. Ahrendt, P. Baumgartner and H. de Neville, eds., Proceedings of the CADE-20 Workshop on Disproving-Non-Theorems, Non-Validity, Non-Provability pages 1727, Tallinn, Estonia, 2005. 3. J. Gow. The Dynamic Creation of Induction Rules Using Proof Planning, PhD Thesis, Edinburgh University, 2004; 4. F. Alexandre, K. Bsaı̈es, M. Demba. Predicate Synthesis from Inductive Proof Attempt of Faulty Conjectures. Lecture Notes in Computer Science, Vol. 3018, Germany, pp. 20-33, 2003; 5. G. Steel. Discovering Attacks on Security Protocols by Refuting Incorrect Inductive Conjectures, PhD Thesis, Edinburgh University, 2003. • I. Razo-Zapata, C. Mex-Perera, and R. Monroy. Masquerade Attacks Based on User’s Profile. Journal of Systems and Software 85(11):26402651, Elsevier, 2012. 1. S. Sen. Using instance weighted naive bayes for adapting concept drift in masquerade detection. International Journal of Information Security 13(6):583-590, Springer, 2014. 2. S. Sen. Sequence-based masquerade detection for different user groups. Security and Communication Networks, Wiley, 2014. 3. P. B. Ruthven. Contextual Profiling of Homogeneous User Groups for Masquerade Detection. Unpublished MSc thesis, Gjφvik University, 2014. 41 4. C. J. Tucker. Performance Metrics for Network Intrusion Systems. Unpublished PhD thesis. University of Plymouth, 2013. • Raúl Monroy. The Use of Abduction to Correct Faulty Conjectures. Unpublished MSc. University of Edinburgh. 1994. 1. Moa Johansson, Lucas Dixon and Alan Bundy. Conjecture Synthesis for Inductive Theories. Journal of Automated Reasoning (to appear) DOI: 10.1007/s10817-010-9193-y. 2010. Springer. 2. Moa Johansson. Automated Discovery of Inductive Lemmas. Unpublished PhD Thesis. University of Edinburgh. 2009. 3. G. Steel. Discovering Attacks on Security Protocols by Refuting Incorrect Inductive Conjectures, PhD Thesis, Edinburgh University, 2003. 4. Graham Steel. Non-theorems and Cryptographic Protocols. Unpublished PhD Thesis Proposal. Edinburgh University, 2002. • R. Saab, R. Monroy and F. Godı́nez. Towards a Model for an Immune System. In Coello-Coello, C., de Albornoz, A., Sucar, L.E. and Battistutti, O.C., eds., Proceedings of the 2nd Mexican Internation Conference on Artificial Intelligence, MICAI‘02, LNAI vol. 2313, pages 401-410, Mérida, Mexico, 2002. Springer-Verlag. Best Paper Award Recipient. 1. M. Villalobos-Arias, C. A. Coello-Coello, O. Hernández-Lerma. Convergence Analysis of a Multiobjective Artificial Immune System Algorithm. Lecture Notes in Computer Science, Vol. 3239, Germany, pp. 226-235, 2004; 2. N. Cortez. Sistema inmune artificial para solucionar problemas de optimización. PhD Thesis. Centro de Investigación y de Estudios Avanzados del Instituto Politécnico Nacional (CINVESTAV), 2004; 3. M. Villalobos-Arias. Análisis de Heurı́sticas de Optimización para Problemas Multiobjetivo. PhD Thesis. Centro de Investigación y de Estudios Avanzados del Instituto Politécnico Nacional (CINVESTAV), 2004. • R. Monroy, R. Saab and F. Godı́nez. On Modelling an Immune System. Computación y Sistemas. 7(4):249–259, 2004. 1. Panagiotis Papadopoulos. Understanding the Function of the Immune System of the Human Body with the Development of a Mathematical Model, Unpublished MSc Thesis, Imperial College London, 2010. 2. H.-W. Mo. Research of immune system response based on partial differential equation. Computer Engineering and Applications 45(11):14. 11 Apr. 2009. 42 3. Y. Abdelgadir and A. Abdullah. Biologically Inspired Model for Securing Hybrid Mobile Ad Hoc Networks. In Proceedings of International Symposium on the Information Technology, 2008. ITSim 2008, pages 1-6, 2008. IEEE Computer Science Press. • K. A. Garcı́a, R. Monroy, L. A. Trejo, C. Mex-Perera, and E. Aguirre. Analyzing Log Files for Post-mortem Intrusion Detection. Journal of IEEE Transactions on Systems, Man, and Cybernetics — Part C 42(6):16901704. IEEE Computer Press, 2012. 1. K. Ethala, R. Sheshadri, and S.-S. Chakkaravarthy. WIDS RealTime Intrusion Detection System Using Entrophical Approach. Artificial Intelligence and Evolutionary Algorithms in Engineering Systems. Springer India, 2015. 73-79. 2. Layman, L., Diffo, S. D., & Zazworka, N. (2014, April). Human factors in webserver log file analysis: a controlled experiment on investigating malicious activity. In Proceedings of the 2014 Symposium and Bootcamp on the Science of Security (p. 9). ACM. 3. Butun, I., Morgera, S., & Sankar, R. (2014). A Survey of Intrusion Detection Systems in Wireless Sensor Networks. Communication Surveys and Tutorials 16(1):1-17. • Raúl Monroy. A Process Algebra Model of the Immune System. In M.G. Negoita, editor, Proceedings of the 8th Knowledge-Based Intelligent Information & Engineering Systems, KES‘04, LNAI Vol. 3214, pages 526533, Wellington, New Zealand, September 2004. Springer-Verlag. 1. V. Narang, J. Decraene, S. Yoon Wong, B. S. Aiswarya, A. R. Wasem, S. Rong Leong and A. Gouaillard. Systems immunology: a survey of modeling formalisms, applications and simulation tools. Immunologic Research 53(1-3):251-265, 2012. Springer. 2. C. McCaiga, R. Normana, and C. Shankland. From individuals to populations: A mean field semantics for process algebra. Theoretical Computer Science 412(17):1557-1580, April 2011. 3. A. Nash and S. Kalvala. A framework proposition for cellular locality of Dictyostelium modelled in π-Calculus. In proceedings of the 2nd Complex Systems Modelling and Simulation (CoSMoS) Workshop, pages 83 - 100, 2009. Luniver Press. • R. Monroy, A. Bundy, and I. Green. Planning Proofs of Equations in CCS. Journal of Automated Software Engineering 7(3):263–304, 2000 1. Bernhard Gramlich. Strategic Issues, Problems and Challenges in Inductive Theorem Proving. Electronic Notes in Theoretical Compututer Science 125(2): 5-43 (2005); 2. L.-A. Fredlund. A Framework for Reasoning about erlang Code. PhD Thesis. Royal Institute of Technology. Sweden, 2001. 43 • R. Monroy and M. Carrillo. Automatic Formulation of Security Properties Under the Inductive Approach. In M.H. Hamza, editor, Proceedings of IASTED‘03, Applied Informatics-Software Engineering, pages 1020-1025, Innsbruck, Austria, 2003. Acta Press. 1. Anitha, D., & Punithavalli, M. (2009). A Survey of Secure Group Key Management. Networking and Communication Engineering 1(7):422-429. 2. G. Steel and A. Bundy. Attacking Group Protocols by Refuting Incorrect Inductive Conjectures. Journal of Automated Reasoning, special issue on Automated Reasoning for Security Protocol Analysis. Kluwer 2005 (to appear). 3. G. Steel and A. Bundy. Attacking a Group Multicast Key Management Protocol using CORAL. Electronic Notes in Theoretical Computer Science 125(1):125-144. • C. Mex-Perera, R. Posadas, J.-A. Nolazco, R. Monroy, A. Soberanes and L. Trejo. An improved Non-negative Matrix Factorization Method for Masquerade Detection. In, R. Vázquez and J.-A. Dı́az, eds., Proceedings of the 1st Mexican International Conference on Informatics Security, MCIS 2006, Mexico, 2006. 1. L. Huang, and M. Stamp. Masquerade detection using profile hidden Markov models. Computers and Security (2011) doi:10.1016/j.cose.2011.08.003. 2. Maximiliano Bertacchini and Pablo Fierens. A Survey on Masquerader Detection Approaches. In Proceedings of V Congreso Iberoamericano de Seguridad Informática, pages 46-60, Montevideo, Uruguay. Universidad de la República de Uruguay, 2008. ISBN: 978-9974-00593-8. • R. Monroy and A. Bundy. On the correction of faulty formulae. Computación y Sistemas, 5(1):25-37, 2001. 1. R. Zarrad, M. Demba, and K. Bsaies. Prouvabilité et correction des formules implicatives. Quatrièms Journées Francophones de Programmation par Contraintes (2008):391-395. INRIA, 2008. 2. Fiona McNeill Dynamic Ontology Refinement. Unpublished PhD Thesis, University of Edinburgh, 2006. • R. Monroy. Concept Formation via Proof Planning Failure. In R. Nieuwenhuis and A. Voronkov, eds., Proceedings of the 8th International Conference in Logic for Programming, Artificial Intelligence and Reasoning, LPAR‘01, LNAI Vol. 2250, pages 718-731, La Havana Cuba, 2001. Springer-Verlag. 44 1. Alan Bundy. Cooperating Reasoning Processes: More than just the Sum of their Parts. In Proceedings of IJCAI’2007, pp. 2-11, Morgan Kaufmann, 2007; • J.C. López and R. Monroy. A Rippling-Based Difference Reduction Technique to Automatically Prove Security Protocol Goals. In C. Lemaı̂tre, C.A. Reyes and J.A. Gonzales, eds., Proceedings of the IX Ibero-American Conference on Artificial Intelligence, IBERAMIA 2004, LNAI Vol. 3315, pages 364-374, Puebla, Mexico, 2004. Springer-Verlag. 1. Bernhard Gramlich. Strategic Issues, Problems and Challenges in Inductive Theorem Proving. Electronic Notes in Theoretical Computer Science 125(2): 5-43 (2005). • F. Godı́nez, D. Hutter and R. Monroy. Audit File Reduction Using NGram Models. In A. Patrick and M. Yung, eds., Proceedings of the Ninth International Conference on Financial Cryptography and Data Security, FC‘05, LNCS Vol. 3570, pages 336-341, Roseau, The Commonwealth Of Dominica, 2005. Springer-Verlag. 1. Ulf Larson. Aspects of Adapting Data Collection to Intrusion Detection. BSc Thesis. Chalmers University of Technology. Göteborg, Sweden, 2006. • R. Monroy, A. Bundy, and I. Green. On process equivalence = equation solving in CCS. Journal of Automated Reasoning 43(1):53-80, Springer, 2009. 1. Popescu, Andrei. Contributions to the theory of syntax with bindings and to process algebra. Unpublished PhD Thesis. University of Ottawa, 2010. 2. Andrei Popescu and Elsa Gunter. Incremental pattern-based coinduction for process algebra and its Isabelle formalization. In, C.-H. L. Ong, ed., Proceedings of FOSSACS 2010. LNCS Vol. 6014 • J. B. Camiña, C. Hernández-Gracidas, R. Monroy and L. Trejo. The Windows-Users and -Intruder simulations Logs Dataset (WUIL): An Experimental Framework for Masquerade Detection Mechanisms. Expert Systems with Applications, Methods and Applications of Artificial and Computational Intelligence. 41(3):919 - 930. 2014. 1. P. B. Ruthven. Contextual Profiling of Homogeneous User Groups for Masquerade Detection. Unpublished MSc thesis, Gjφvik University, 2014. • D. Hutter and R. Monroy. On the automated correction of protocols with improper message encoding. In, L. Vigan‘o and P. Degano, eds., Proceedings of the Joint Workshop on Automated Reasoning for Security Protocol Analysis and Issues in the Theory of Security, ARSPA-WITS’09, LNCS Vol. 5511, pages138-154. Springer, 2009. 45 1. W. Song and B. Hu. Approach to Detecting Type-Flaw Attacks Based on Extended Strand Spaces. The Computer Journal (2014): bxu106. • Juan C. López P., Raúl Monroy and Dieter Hutter. On the Automated Correction of Security Protocols Susceptible to a Replay Attack. In, J. Biskup and J. Lopez, eds., Proceedings of the 12th European Symposium Research Computer Security, ESORICS 2007. LNCS Vol. 4734, pages 594-609, Germany, 2007. Springer. 1. B. Bonakdarpour, R. Hajisheykhi, and S. S Kulkarni. KnowledgeBased Automated Repair of Authentication Protocols. In Formal Methods FM 2014, pp. 132-147, 2014. Springer International Publishing. • R. Monroy and G. Steel. Faulty Group Protocols. Unpublished research report. The University of Edinburgh. 1. L.-A. Lizama, M.-López-Romero, S. Venegas-Andraca, and E. de Carlos-López. Secure transport of UTC (CNM) through quantum key distribution. In Proceedings of the Simposio de Metrologı́a, pages 1-6, 2010. 2. Ashish Rastogi. A Model based approach to Implement Cloud Computing in E-Governance. International Journal of Computer Applications 9(7):15-18, November 2010. 3. S. Sandosh, V. Akila and S. Uthayashangar. Secure Decentralized Group Key Management through Progressive Approach. International Journal of Computer Applications 9(10):6-10, November 2010. 4. Antoine Mercier. Contributions à l’Analyse Automatique des Protocoles Cryptographiques en Prśence de Propriétés Algébriques: Protocoles de Groupe, Équivalence Statique. Unpublished PhD Thesis. École Normale Supérieure de Cachan, 2009. 46
© Copyright 2026